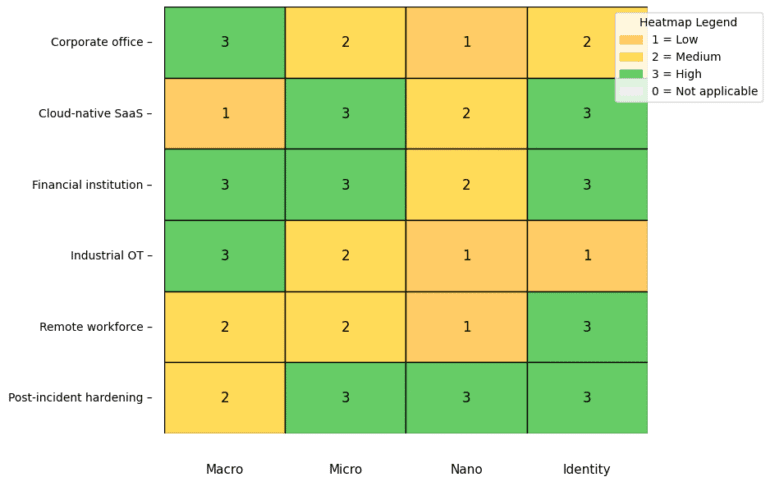
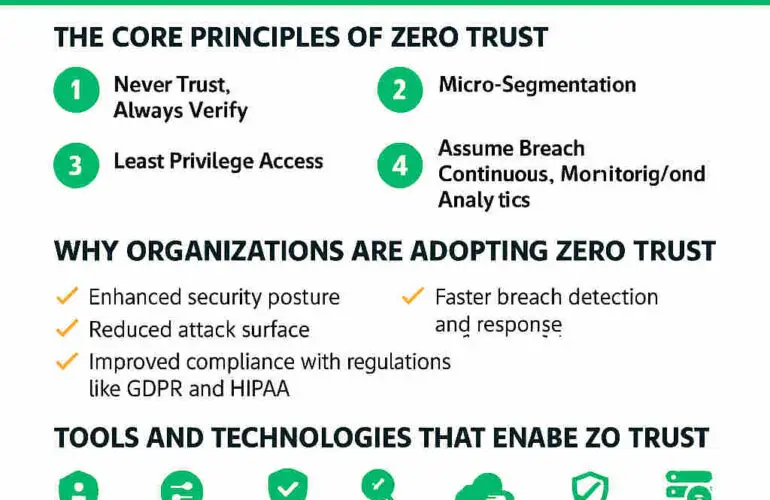
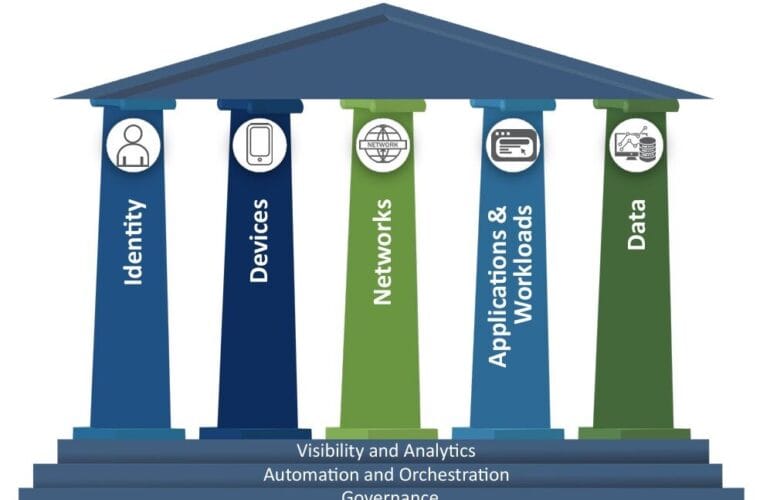
Zero Trust is a security paradigm – never assumes trust, requiring continuous verification. At its heart lies identity segmentation, which shifts access control from network topology to the identity and context of the requester. This post unpacks the core principles of Zero Trust, defines identity segmentation, contrasts it with traditional network segmentation, and explores the advantages of each.
Zero Trust Core Principles
Zero Trust mandates three foundational tenets:
- Verify explicitly by authenticating and authorising based on identity, device health, location, and other signals.
- Enforce least-privilege access through just-in-time and just-enough permissions.
- Assume breach by segmenting resources and continuously monitoring to minimise impact .
What Is Identity Segmentation?
Identity segmentation grants or denies access based on who (or what) is requesting resources, rather than where it resides on the network. It dynamically binds access policies to user and device identities, adapting in real time to changing contexts like location or risk score. This approach isolates interactions, ensuring a compromised identity can’t freely move laterally across systems.
What Is Network Segmentation?
Network segmentation divides a network into smaller zones—often by VLANs, subnets, or firewall policies—to contain threats within a segment. It relies on IP addresses and network boundaries to restrict traffic flows, limiting the blast radius of an intrusion but lacking insight into which specific user or process initiated the connection.
Key Differences: Identity vs. Network Segmentation
- Basis of Control
- Identity: Access rules tied to user, device, or service identity.
- Network: Access rules tied to IP addresses, ports, and network segments.
- Granularity
- Identity: Process-level, context-aware enforcement.
- Network: Coarse, network-layer enforcement.
- Adaptability
- Identity: Dynamic policies that follow roaming users and cloud workloads.
- Network: Static rules that require manual updates for topology changes.
Advantages of Identity Segmentation
- Lateral Movement Protection
Isolates each identity so a compromised credential can’t hop freely between resources. - Context-Aware Access
Factors in device posture, location, and risk signals to adjust permissions in real time. - Reduced Attack Surface
Applies micro-policies per identity, minimising open paths across the environment.
Advantages of Network Segmentation
- Simplicity of Deployment
Leverages existing VLANs, subnets, and firewalls without overhauling identity systems. - Performance Isolation
Contains broadcast domains and limits traffic scope for improved network performance. - Regulatory Compliance
Eases demonstration of segmented environments for standards like PCI DSS or HIPAA.
Conclusion
Identity segmentation extends Zero Trust by enforcing least-privilege access at the identity and process level, far beyond what network boundaries alone can offer. While network segmentation remains a valuable tool for containment and compliance, pairing it with identity-driven controls ensures adaptive, context-aware security. To embark on this journey, evaluate your IAM capabilities, map critical assets to identity groups, and pilot identity segmentation alongside existing network controls.