5 Key Strategies for Lateral Movement Defence in Network Security
When cybercriminals gain access to an organisation’s infrastructure, they often attempt to expand their reach by moving between systems, searching for sensitive information, and increasing their privileges. This sideways navigation allows adversaries to avoid detection and broaden the impact of their intrusion. Slowing or preventing this internal progression is crucial for limiting damage, containing threats, and safeguarding critical assets. For more on cyber security trends, see Cyber Security Insights.
Understanding how Attackers use Lateral Movement Within Networks
Once an intruder establishes an initial presence—commonly through phishing, exploiting vulnerabilities, or stealing credentials—they rarely target high-value systems immediately. Instead, they may:
- Map out the network to identify connections and potential routes. See NIST Cybersecurity Framework for standards.
- Gather additional login details from compromised devices or memory-resident tools. Learn about identity management at What is IAM?.
- Use legitimate administrative protocols (such as Windows Remote Management, RDP, or SSH) to access other servers and workstations. Explore endpoint protection at Microsoft Security Documentation.
- Gradually increase their access rights to reach protected areas or confidential data.
This stealthy approach enables malicious actors to blend in with normal activity, bypass perimeter defences, and reach critical systems without triggering alarms. For attacker techniques, see MITRE ATT&CK Framework.
The Importance of Containing Internal Threats
Limiting an attacker’s ability to traverse a network can turn a single compromised device into a contained incident, rather than a widespread breach. Effective containment:
- Reduces the likelihood of data theft or exfiltration.
- Shortens the time an attacker remains undetected, enabling faster response. Learn about threat exposure at Continuous Threat Exposure Management.
- Restricts the number of systems at risk if an intruder’s movement is blocked.
- Discourages further exploration and lowers the risk of ransomware deployment.
Organisations that successfully restrict unauthorised internal access are more likely to detect breaches early, isolate affected machines, and restore normal operations quickly.
Common Methods Used by Adversaries
- Pass-the-Hash and Pass-the-Ticket: Using stolen authentication data to access new hosts without needing actual passwords. See MITRE ATT&CK Framework for details.
- Remote Execution Tools: Misusing utilities like PsExec, WinRM, SSH, and WMI for covert command execution.
- Credential Dumping: Extracting passwords, hashes, or tokens from memory or local storage with tools such as Mimikatz.
- Golden and Silver Ticket Attacks: Forging Kerberos tickets to impersonate users or domain controllers, granting extended access.
- Living Off the Land: Leveraging built-in operating system tools (e.g., PowerShell, certutil, regsvr32) to avoid detection by security software.
Recognising these tactics is the first step towards designing effective defences at every stage of an attack. For more on segmentation within a corporate network see Network Segmentation Corporate.
5 Defensive Strategies to Restrict Attacker Movement
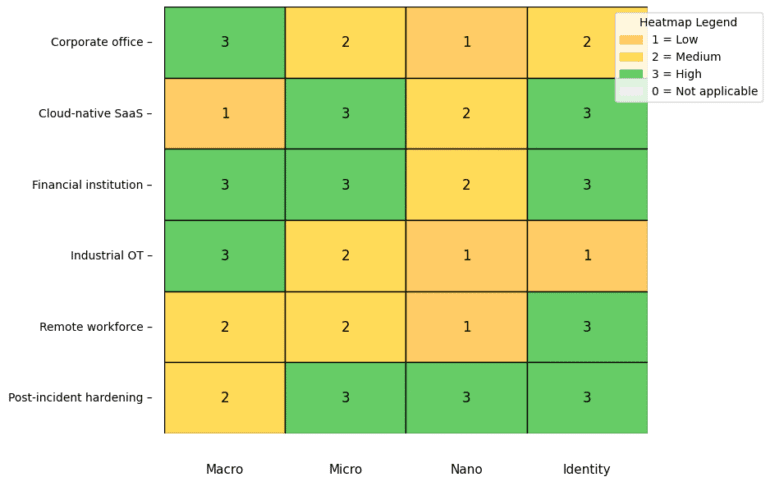
- Network Segmentation: Divide infrastructure into security zones and enforce strict access controls between them. Limit the number of systems any single account can reach. Learn more about the importance of identity data quality at Importance of Identity Data Quality.
- Principle of Least Privilege: Ensure users and service accounts have only the permissions necessary for their roles. Regularly review and remove unnecessary access rights. For zero trust, see What is Zero Trust?.
- Multi-Factor Authentication (MFA): Require additional verification for remote access and privileged accounts. Even if credentials are compromised, a second factor can prevent unauthorised entry.
- Credential Management: Rotate service account passwords frequently and isolate administrative accounts on dedicated hosts not used for general activities.
- Monitoring and Alerts: Deploy endpoint detection and response (EDR) solutions to track process execution, network connections, and credential use. Set up alerts for unusual behaviour, such as the use of attacker tools or attempts to extract credentials.
Best Practices for Ongoing Protection
- Conduct regular penetration testing and red-team exercises to assess your segmentation and detection capabilities.
- Adopt a zero-trust approach, ensuring every request is authenticated and authorised, regardless of its origin. For a roadmap, visit Prepare a Zero Trust Roadmap.
- Maintain an accurate inventory of assets and network interconnections.
- Train employees to recognise phishing attempts and suspicious activity.
- Develop clear incident response procedures, including steps for isolating devices suspected of being compromised.
Conclusion
The ability of attackers to move within a network is a critical phase of many cyber incidents. By implementing segmentation, enforcing least privilege, requiring MFA, and maintaining vigilant monitoring, organisations can significantly reduce the impact of intrusions and improve early detection. A layered, proactive defence not only frustrates adversaries but also provides valuable time for response teams to act. For implementation approaches, visit Approach Implementing Zero Trust.
In addition to these measures, consider exploring advanced techniques such as micro-segmentation, machine-learning-based anomaly detection, and deception technologies like honeypots and canary tokens. Embracing zero-trust principles and automating response processes will further strengthen your organisation’s resilience against sophisticated threats.