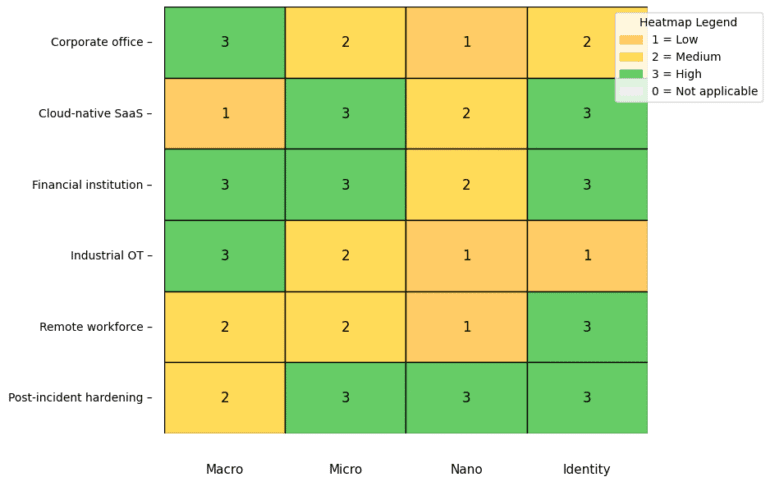
New technology concepts and working practices are redefining the network security perimeter in a zero trust world. Organisations can no longer rely on a single, static boundary around their networks. As cloud services proliferate, workforces disperse and Internet-enabled devices multiply, the old castle-and-moat model has broken down. By 2025, zero trust has become the cornerstone of network security. Rather than trusting all traffic inside a perimeter, every access request is scrutinised. This new architecture redefines the perimeter as a dynamic, context-driven construct tailored to identities, devices, applications, workloads and data.
From Static Boundaries to Fluid, Contextual Defences – New technology concepts and working practices are redefining the network security perimeter in a zero trust world
The traditional perimeter treated everything “inside” as implicitly safe, defended by firewalls, VPN gateways and demilitarised zones. That fortress mentality fails when users connect from home, when servers live in multiple clouds or when Internet-of-Things (IoT) sensors sit at the edge.
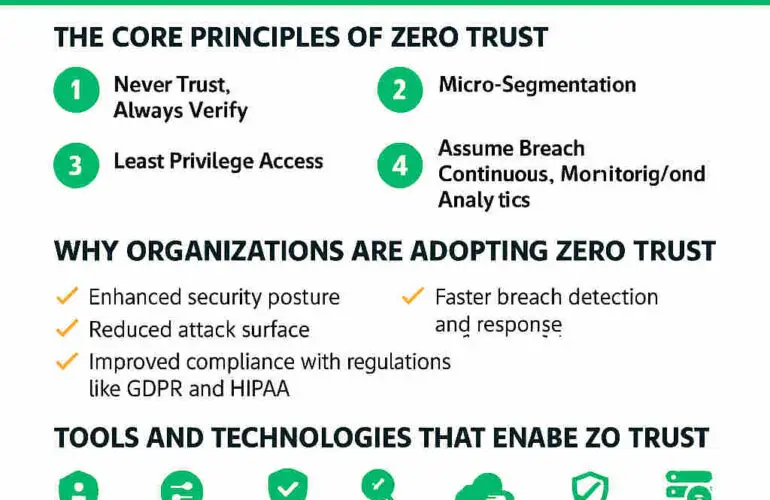
Zero trust flips this script. It assumes no actor or system is trustworthy by default, regardless of where it resides. The result is a perimeter that is:
- Dynamic: Continuously adapting to risk factors such as user behaviour, device health and threat intelligence.
- Micro-segmented: Divided into granular zones based on application sensitivity, compliance or workload function.
- Identity-centric: Focused on who (or what) is requesting access, rather than on network location.
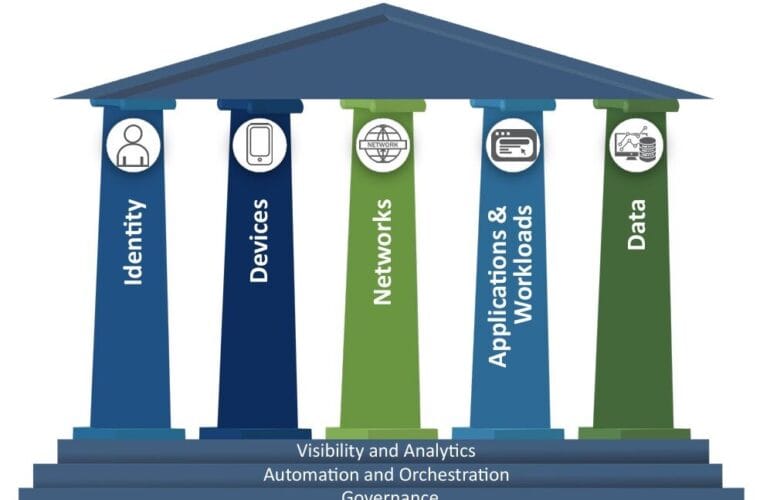
Components of a Modern Zero Trust Perimeter
- Identity Perimeter
Every session begins with an identity. Robust identity and access management (IAM) systems enforce:
- Multifactor authentication (MFA) or passwordless methods
- Risk-based, adaptive authorisation that scales authentication strength to current context
- Just-in-time privilege elevation to grant least-privilege access
- Device Perimeter
Devices must prove their security posture before joining a network or accessing resources. Key capabilities include:
- Endpoint detection and response (EDR) for real-time threat monitoring
- Unified endpoint management (UEM) to enforce configuration baselines
- Continuous posture assessment covering patch levels, anti-malware status and configuration drift
- Network and Micro-segmentation Perimeter
Instead of broad network zones, organisations carve out micro-perimeters around individual applications and data repositories. Software-defined segmentation—whether on-premises or in the cloud—ensures that east-west traffic is inspected and restricted, drastically reducing an attacker’s lateral movement options.
- Application Perimeter
Modern applications, microservices and legacy systems all require zero trust guards. Components include:
- Zero trust network access (ZTNA) gateways that authenticate and authorise per session
- API proxies and service meshes enforcing mutual TLS and fine-grained policy between services
- Deep packet inspection and behavioural analytics for application-layer threats
- Data Perimeter
Data itself carries its own defences. A data-centric perimeter leverages:
- Ubiquitous encryption in transit and at rest
- Data loss prevention (DLP) and digital rights management (DRM)
- Attribute-based access controls (ABAC) so that policies follow the data, not the network
- Workload Perimeter
Workloads now run in VMs, containers, serverless functions and edge sites. A workload perimeter ensures:
- Service identities and mutual authentication between workloads
- Continuous monitoring of inter-workload traffic
- Automated policy updates as applications scale or migrate
Secure Access Service Edge (SASE) and Security Service Edge (SSE)
Secure Access Service Edge (SASE) unites networking (SD-WAN, WAN optimisation) with security (CASB, SWG, ZTNA) into a cloud-native fabric. By 2025, SASE platforms will orchestrate perimeters globally, delivering consistent policy enforcement wherever users and devices connect.
Security Service Edge (SSE) focuses purely on security functions—ZTNA, CASB and data protection services. SSE wraps every session with inspection, threat prevention and data controls, effectively extending the perimeter to each transaction.
Edge-Native Perimeters for Distributed Infrastructure
Edge computing brings compute and storage closer to end users for low-latency use cases. Each edge node becomes a micro-site requiring its own zero trust perimeter:
- Embedded ZTNA clients on user devices establish secure tunnels to edge points of presence.
- Lightweight policy enforcement points at each edge location inspect, segment and route traffic.
- Federated identity proxies ensure consistent access decisions, even when central cloud links are intermittent.
The Perimeter of One: Session-Specific Boundaries
The “Perimeter of One” concept tailors defences per user-device-application session. AI-driven analytics and real-time telemetry enable:
- Fine-grained least-privilege access, scoped to the exact resource and task
- Adaptive policy levels adjusting authentication strength, session duration or re-authentication triggers based on risk
- Variable inspection depth balancing security scrutiny and user experience
This customisation minimises friction for trusted scenarios while tightening controls when risk spikes.
Securing IoT and Operational Technology (OT)
IoT and OT devices often run legacy protocols on constrained hardware. Zero trust perimeters for these environments include:
- Hardware roots of trust via TPM modules or secure elements
- Network behaviour analytics profiling normal device communications
- Micro-segmented OT zones separating control, telemetry and management planes with strict gateways
These measures replace reliance on mere network isolation and enable continuous, context-aware verification.
AI-Driven Orchestration and Continuous Verification
By 2025, artificial intelligence and machine learning are integral to perimeter management:
- Anomaly detection engines establish dynamic baselines for user, device and network behaviour
- Security orchestration, automation and response (SOAR) platforms execute automated remediation—quarantining endpoints or updating policies when threats emerge
- Adaptive policy tuning refines access rules based on threat intelligence and organisational changes
The perimeter thus evolves from static rule sets into an autonomous, self-learning defence system.
Data-Centric Defences: Protecting the Crown Jewels
Networks may be breached, but data must remain protected. A data-centric perimeter ensures:
- Centralised key management governing encryption policies
- Contextual data wrappers enforcing usage constraints regardless of location
- Data fingerprinting and tracking to locate and govern copy proliferation across clouds and endpoints
In effect, each data object carries its own micro-perimeter that persists beyond network boundaries.
Balancing Security and User Experience
Zero trust is not about piling on friction. It’s about risk-based access that tailors user experience:
- Low-risk users on managed devices enjoy passwordless single sign-on
- High-risk scenarios—such as off-hours access from untrusted devices—trigger stronger multi-factor steps or temporary lockdowns
This friction-modulated approach preserves productivity while maintaining robust defence.
Emerging Innovations Shaping Future Perimeters
- Quantum-resistant cryptography embedded in identity and data layers
- Blockchain-anchored identity fabrics enabling decentralised trust without central credential stores
- User-Managed Access (UMA) where data owners define personal sharing policies, creating micro-perimeters around individual information
- Homomorphic encryption allowing computation on encrypted data within the perimeter without exposing plaintext
These advancements will blur the lines between internal and external, forging ever more adaptive, resilient defences.
Conclusion: Earning Your Perimeter Every Session
In a zero trust era, the network perimeter transforms into a living ecosystem of policies, agents, analytics and cryptography. By 2025 and beyond, defences will be:
- Dynamic and context-driven
- Micro-segmented around identities, devices, workloads, applications and data
- Orchestrated by AI for continuous verification and automated response
The secure perimeter is no longer a line on a diagram. It’s a session-by-session contract of trust that organisations must continually earn and renew to stay ahead of sophisticated adversaries.
The sequence of pie charts from 2020 through 2028 reveals a marked shift in how organisations protect their environments. Where once traditional network perimeter firewalls dominated, today—and increasingly into the latter half of the decade—the emphasis is squarely on identity and AI-driven orchestration to establish dynamic ring-fences around critical assets.
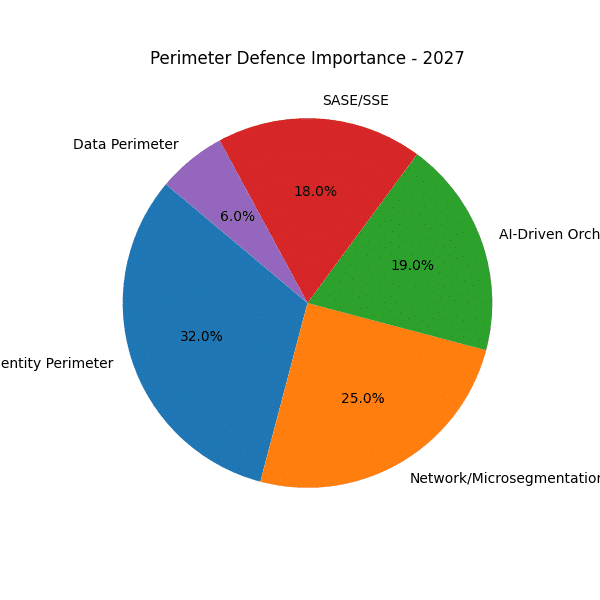
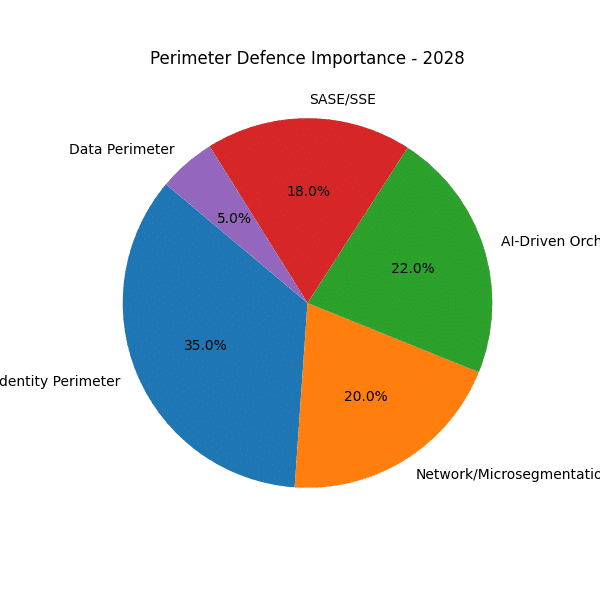
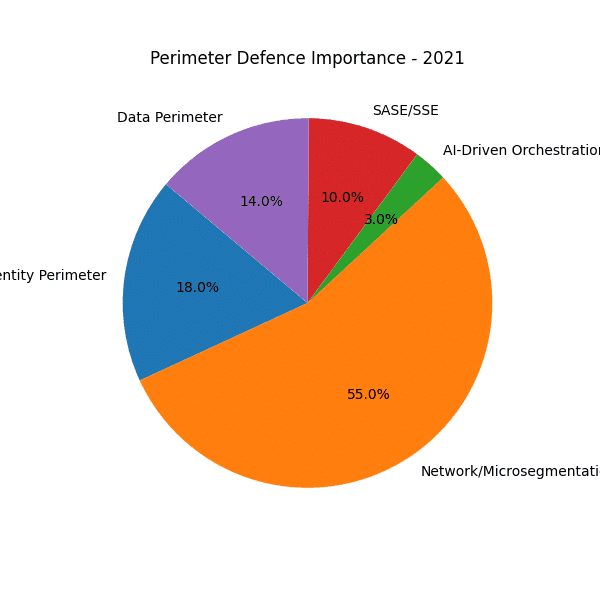
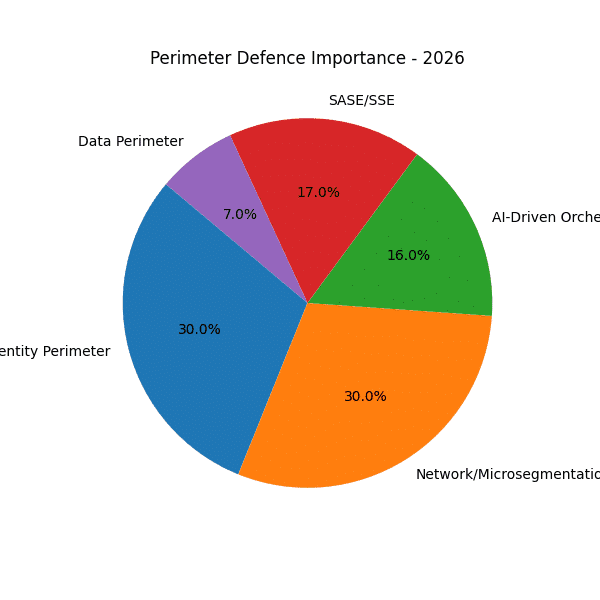
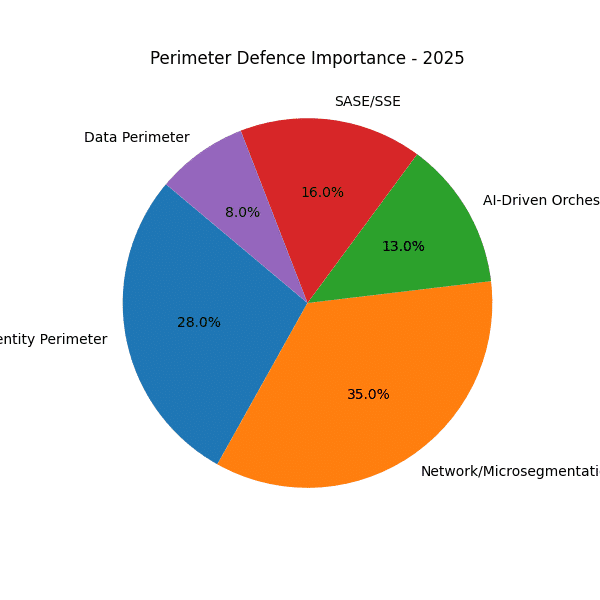
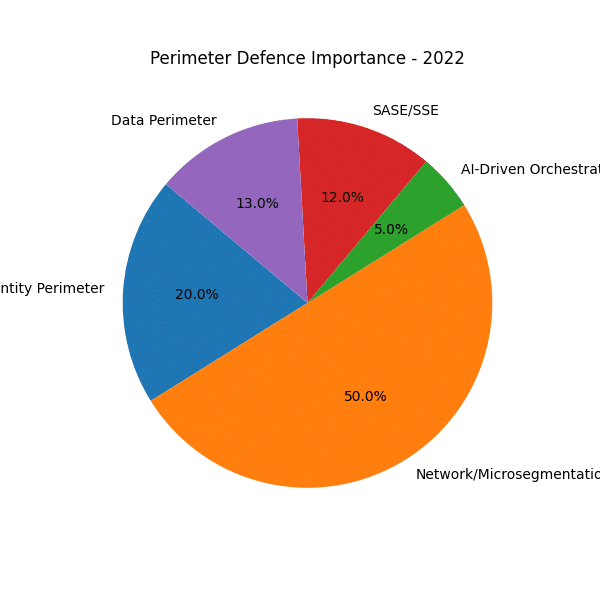
Traditional Network Firewalls in Decline
- 2020–2022 dominance
Between 2020 and 2022, the network/micro-segmentation perimeter (firewalls, VPN gateways, DMZs) consistently accounted for over half of all perimeter defence importance. It reflected the lingering confidence in castle-and-moat models, where traffic “inside” was trusted once past the perimeter. - Gradual erosion (2023–2024)
By 2023, that share dips below 50% and continues its downward trajectory into 2024. Organisations begin to accept that a hard network edge cannot encompass distributed users, cloud workloads or IoT devices.
Surge of Identity-Centric Controls
- Growing share from 2021
Identity perimeter defences (IAM, MFA, adaptive authentication) grew steadily from around 15% in 2020 to roughly 25% by 2024. - Projected leadership by 2025
Forecasts show identity controls surpassing all other categories after 2025, climbing to over 30% by 2028. This underscores the realisation that who or what is requesting access is the new perimeter.
Emergence of AI-Driven Orchestration
- From niche to necessity
In 2020, AI-driven orchestration barely registers (practically 0%), but by 2024 it represents about 10% of perimeter focus. - Rapid acceleration (2025–2028)
Predictions indicate this category will double to around 20% by 2028. Automated anomaly detection, dynamic policy tuning and self-healing playbooks are becoming indispensable for continuous verification.
Supporting Trends
- SASE/SSE expands from a minor slice in 2020 to a major pillar by 2028, reflecting consolidation of networking and security in the cloud.
- Edge-native perimeters and Workload perimeters grow modestly as organisations deploy compute closer to users and orchestrate containerised services.
- Data-centric defences (encryption, DLP, DRM) gain steadier momentum, reinforcing the notion that data should carry its own protective boundary.
Key Takeaway
The charts make one fact crystal clear: network firewalls remain relevant but are no longer the sole guardians of the enterprise. From 2025 onwards, identity and AI-orchestration will form the primary ring-fence, dynamically verifying every session and shrinking trust zones to the individual user, device and workload. This evolution marks the final departure from the static perimeter of old, ushering in a truly adaptive, zero-trust era.