Discover how macro, micro, nano, and identity-based approaches can protect your organisation’s digital infrastructure, reduce cyber risk, and support compliance with regulatory requirements. This comprehensive guide explores various methods, implementation options, and best practices for businesses seeking robust security and Zero Trust adoption.
Network Segmentation Strategies – An Overview
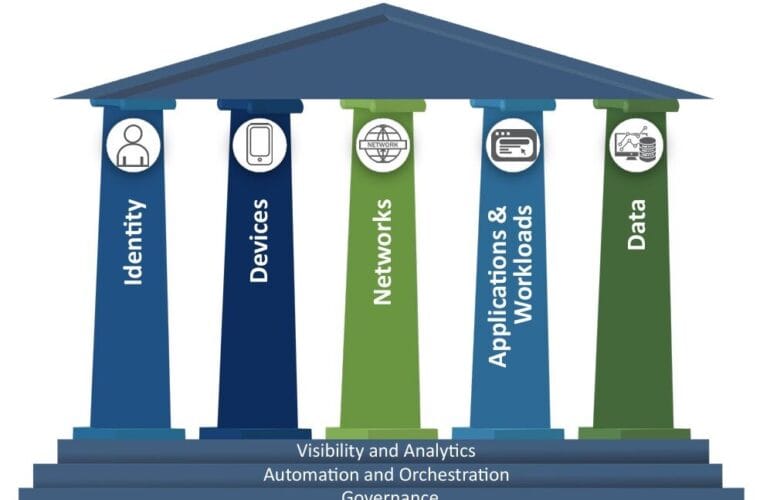
Dividing a corporate environment into smaller, isolated segments is a proven way to minimise attack surfaces, enhance performance, and enforce security policies. Techniques such as macro, micro, nano, and identity-based segmentation address specific threats and operational needs. Effective partitioning is essential for data protection, compliance, and operational technology in modern enterprises.
Macro Segmentation
What Is Macro Segmentation?
Macro segmentation creates large trust zones, including corporate LANs, guest networks, data centres, cloud VPCs, and remote VPNs. It’s ideal for organisations needing broad separation for compliance or those with distinct trust domains.
Implementation Options
- VLANs and routed subnets with ACLs
- Physical separation for high-assurance enclaves
- Dedicated firewalls and DMZs
- Cloud-native VPC/VNet boundaries
Strengths & Weaknesses
- Strengths: Simple design, legacy tool support, effective for initial best practices.
- Weaknesses: Coarse controls, risk of lateral movement within zones.
Best Practice
Use this approach for initial design, regulatory compliance, and environments with clear trust boundaries, such as financial institutions and industrial control systems.
Micro Segmentation
What Is Micro Segmentation?
Micro segmentation restricts east-west traffic within network segments, focusing on workloads and applications. This technique is critical for cloud security and detailed control in cloud environments.
Implementation Options
- Host-based firewalls (e.g., iptables, Windows Firewall)
- SDN controls (VMware NSX, Azure Firewall Manager)
- Service mesh with mTLS
- Container network policies
Strengths & Weaknesses
- Strengths: Limits lateral movement, supports cloud-native architectures, improves overall security.
- Weaknesses: Operational complexity, policy management challenges.
Best Practice
Prioritise this method for sensitive workloads, cloud deployments, and post-incident hardening.Nano Segmentation
What Is Nano Segmentation?
Nano-level controls apply policy at the process or port level within containers or hosts, providing maximum granularity. This is essential for protecting critical infrastructure and high-value systems.
Implementation Options
- EDR/XDR with application control
- Container runtime security
- Process-level firewalls and ZTNA agents
Strengths & Weaknesses
- Strengths: Precise control, reduced attack surface, ideal for safeguarding critical endpoints.
- Weaknesses: High operational burden, complex policies.
Best Practice
Use this for high-value systems, critical infrastructure, and environments requiring advanced protection.
Identity Segmentation
What Is Identity Segmentation?
Identity segmentation uses user, device, and application identity for access control, moving beyond IP-based policies. It’s vital for remote workforce security and Zero Trust implementation.
Implementation Options
- Zero Trust Network Access (ZTNA)
- Conditional access with IdP and device management
- OAuth/OpenID Connect, mutual TLS
- Privileged Access Management (PAM)
Strengths & Weaknesses
- Strengths: Flexible, scalable, user-centric, supports hybrid and remote workforces.
- Weaknesses: Requires strong identity hygiene, integration complexity.
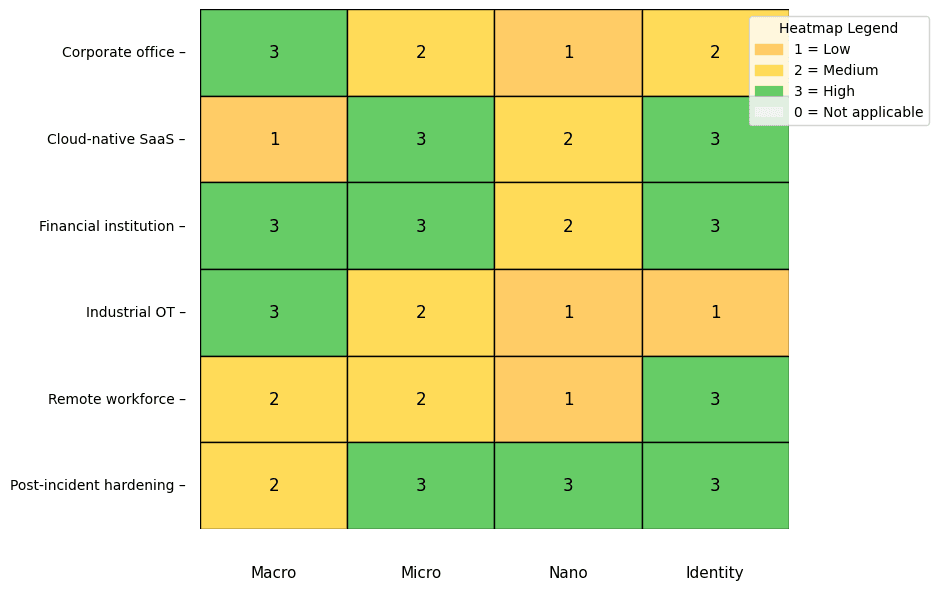
Use Cases & Priorities
- Corporate office: Broad separation for network, identity-based controls for remote access, detailed controls for critical services.
- Cloud-native SaaS: Detailed and identity-based controls, nano-level for critical data stores.
- Financial institution: Broad separation for cardholder data, detailed/nano for PII servers, identity for privileged access.
- Industrial control systems: Physical/broad separation between IT/OT, detailed controls at DMZ gateways, selective nano for PLCs.
- Remote/hybrid workforce: Identity-based controls, broad separation for cloud resources, detailed controls for admin workstations.
- Post-incident hardening: Detailed controls for east-west restriction, nano for compromised hosts, identity for privileged accounts.
Implementation Roadmap & Best Practice
- Assess and classify assets for best practices.
- Define policy model for segmentation strategies.
- Pilot and iterate in high-risk areas, such as financial institutions and industrial control systems.
- Automate policy lifecycle with CI/CD.
- Monitor and verify compliance with regulations.
- Coordinate identity and device management for remote workforce.
- Prepare operations and support teams for Zero Trust adoption.
Frequently Asked Questions
- What Is Segmentation in Network Security?
- Dividing a network into smaller segments to improve security and performance.
- Which Type Should I Use?
- It depends on your business risk, regulatory requirements, and operational capacity. Most organisations benefit from a layered approach using a combination of these methods.
- How Does Identity-Based Segmentation Support Zero Trust?
- It enforces access based on identity and context, reducing reliance on network boundaries and supporting remote workforce security.