Zero Trust Implementation: Approaches & Use Cases
Zero Trust is no longer just a buzzword – it's a strategic imperative. This guide breaks down the most common implementation approaches and how they align with specific use cases.
Understanding the Zero Trust Philosophy
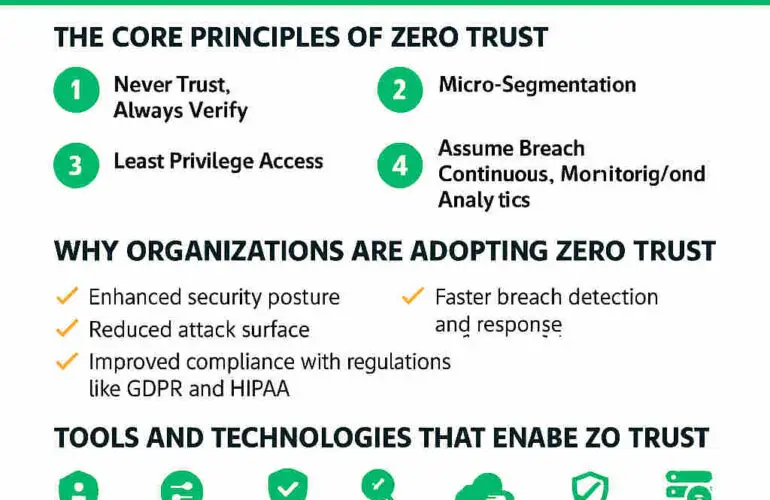
The core idea: “Never trust, always verify.” Learn more about Zero Trust. Zero Trust assumes that threats can exist both inside and outside the network, so every access request must be authenticated, authorised, and continuously validated.
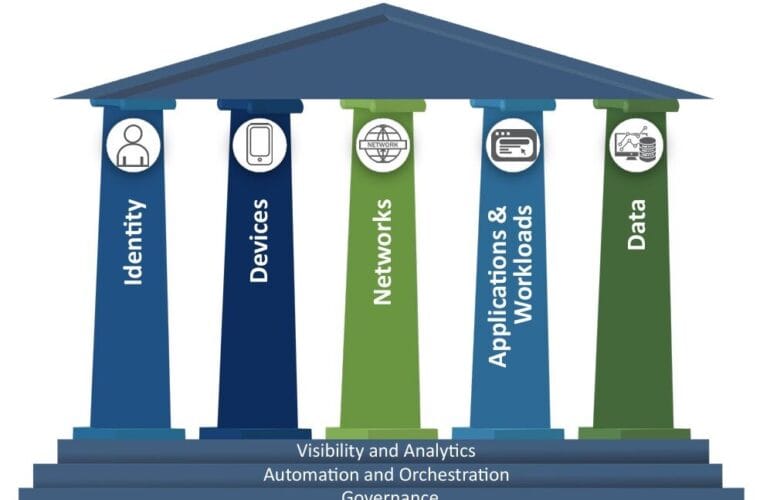
Implementation Approaches by Use Case
1. Identity-Centric Approach
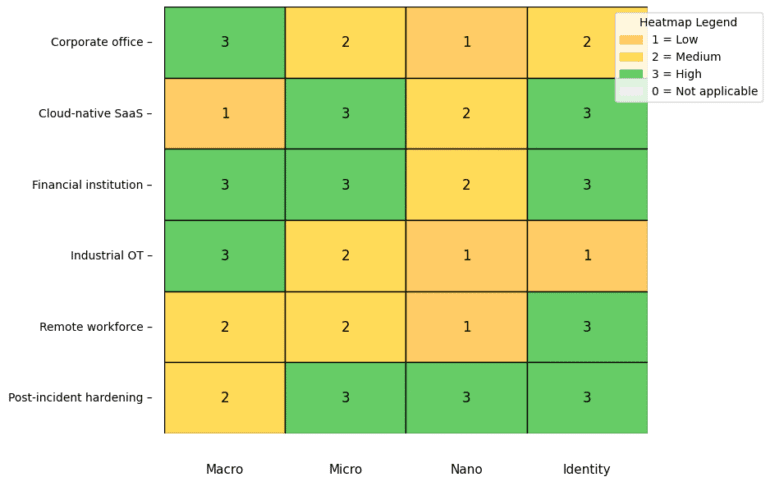
Use Case: Remote workforce, cloud-first organisations, BYOD environments
- Multi-Factor Authentication (MFA)
- Single Sign-On (SSO)
- Identity and Access Management (IAM)
- Conditional Access Policies
Benefits:
- Strong user authentication
- Granular access control
- Seamless user experience across platforms
2. Network-Centric Approach
Use Case: Legacy infrastructure, on-premise data centres, segmented networks
- Microsegmentation
- Software-defined perimeters
- Network Access Control (NAC)
- VPN replacement with ZTNA (Zero Trust Network Access)
Benefits:
- Limits lateral movement of attackers
- Protects legacy systems
- Enhances visibility into network traffic
3. Application-Centric Approach
Use Case: SaaS-heavy environments, DevOps teams, API-driven ecosystems
- Secure Web Gateways (SWG)
- Cloud Access Security Brokers (CASB)
- API gateways with authentication
- Runtime application self-protection (RASP)
Benefits:
- Protects sensitive data in transit and at rest
- Enforces access policies at the app level
- Supports secure DevOps practices
4. Data-Centric Approach
Use Case: Highly regulated industries (finance, healthcare), IP-sensitive organisations
- Data Loss Prevention (DLP)
- Encryption (at rest and in transit)
- Rights Management
- Data classification and tagging
Benefits:
- Ensures compliance with regulations (GDPR, HIPAA, etc.)
- Prevents unauthorised data access and exfiltration
- Enables secure collaboration
5. Device-Centric Approach
Use Case: High-risk endpoints, mobile-heavy environments, IoT deployments
- Endpoint Detection and Response (EDR)
- Mobile Device Management (MDM)
- Device posture checks
- Secure boot and firmware validation
Benefits:
- Blocks compromised or non-compliant devices
- Enforces patching and security policies
- Reduces endpoint vulnerabilities
Hybrid and Phased Approaches
Most organisations adopt Zero Trust in phases, combining elements from multiple strategies based on priorities and maturity.
- Start with identity and access controls, then expand to network segmentation.
- Secure high-value applications first, then scale across the enterprise.
- Implement Zero Trust for remote access, then extend to internal systems.
Metrics for Success
- Visibility: Know who’s accessing what, when, and how.
- Automation: Use AI and machine learning to detect anomalies.
- Policy Enforcement: Ensure consistent policies across environments.
- User Experience: Balance security with usability.
Final Thoughts
Zero Trust is not a destination—it’s a mindset and a continuous journey. By aligning implementation strategies with specific use cases, organisations can build a resilient, adaptive security posture that meets today’s challenges and tomorrow’s threats.