Understanding NIST’s Zero Trust Architecture and Its Key Elements
What is NIST?
NIST’s Special Publication 800-207 defines Zero Trust as an architecture built on two core pillars: continuous verification and least-privilege access. It codifies nine design principles and three logical components—Policy Engine, Policy Administrator, and Policy Enforcement Point—to guide organisations in shifting from perimeter-centric defences to a dynamic, data-centric security model.
What Is NIST SP 800-207?
NIST SP 800-207, released in August 2020, formalises Zero Trust for federal agencies and private-sector adopters. It replaces the notion of a trusted network interior by treating every resource request as coming from an untrusted network. Trust decisions are made per request, based on continuous evaluation of identity, device posture, and risk context.
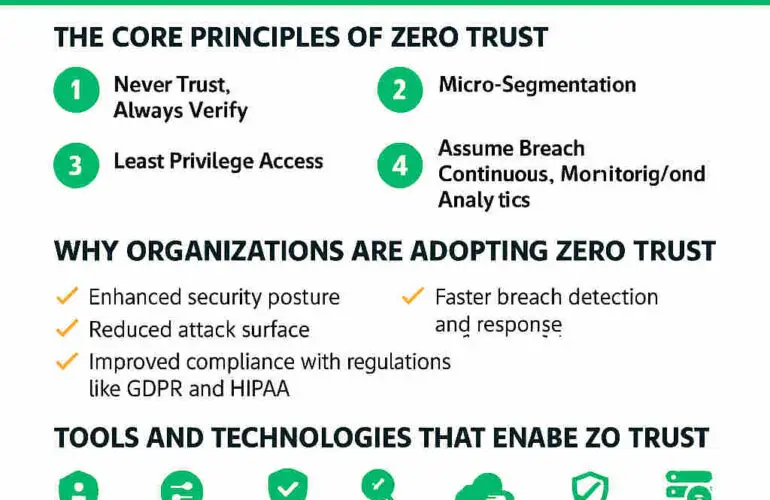
Nine Zero Trust Design Principles
- All data sources and computing services are resources.
- All communication is secured regardless of network location.
- Access to enterprise resources is granted per session.
- Access decisions are based on dynamic policy and observed state.
- The enterprise monitors and measures integrity and security posture of assets.
- Resource authentication and authorisation are dynamic and strictly enforced.
- The enterprise collects and analyses telemetry to improve its security posture.
- Security policies are defined and enforced using automated mechanisms.
- Components are designed for resiliency and assume compromise is inevitable.
Core Logical Components
- Policy Engine (PE): The brain of Zero Trust. It gathers context (user identity, device health, threat intel) and makes centralised trust decisions.
- Policy Administrator (PA): Enacts PE’s decisions by configuring enforcement points—establishing or tearing down secure sessions.
- Policy Enforcement Point (PEP): Gatekeeper that intercepts resource requests and enforces access grants or denials as directed by the PA.
- Some models include a Context Broker to feed the PE real-time telemetry and threat intelligence.
Deployment Models
- Centralised Model: A single PE/PA cluster manages all PEPs, ideal for smaller, tightly controlled environments.
- Distributed Model: Multiple PE/PAs are deployed close to resource clusters, reducing latency for global operations.
- Hybrid Model: Combines central policy definition with localised enforcement, balancing consistency and performance.
Mapping to the NIST Cybersecurity Framework
| CSF Function | How Zero Trust Helps |
|---|---|
| Identify | Continuous asset inventory; classification |
| Protect | Dynamic policy enforcement; least privilege |
| Detect | Real-time telemetry; behaviour analytics |
| Respond | Automated isolation; rapid policy updates |
| Recover | Resilient designs; minimal blast radius |
Implementation Roadmap
- Assess: Inventory assets, data flows, and current trust zones.
- Define Policy: Establish dynamic access policies based on roles, risk levels, and device posture.
- Architect: Design your PE, PA, and PEP topology—centralised, distributed, or hybrid.
- Deploy Controls: Roll out identity controls (IAM, MFA), segmentation (ZTNA, micro-segmentation), and telemetry collectors.
- Enforce & Monitor: Automate policy enforcement, gather continuous telemetry, and refine policies based on observed anomalies.
- Iterate: Use lessons learned and emerging threat intelligence to evolve your Zero Trust posture.
Challenges and Best Practices
- Start small: pilot Zero Trust around a high-value application or remote access scenario.
- Automate: manual policy updates don’t scale; invest in orchestration and AI-driven analytics.
- Align teams: security, network, and operations must share telemetry and policy goals.
- Measure success: track reduction in lateral movement, time to detect anomalies, and policy compliance rates.
Beyond NIST SP 800-207
While SP 800-207 provides the blueprint, real-world Zero Trust deployments often integrate:
- DevSecOps pipelines for continuous policy testing.
- Cloud-native controls (CASB, SWG, CNAPP) to secure dynamic workloads.
- IoT posture management for non-traditional endpoints.
Exploring these areas will deepen your Zero Trust journey and prepare you for adaptive threats.