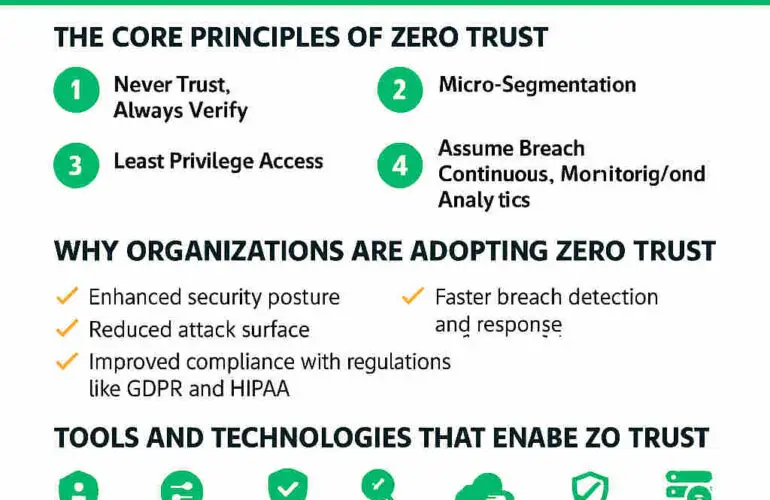
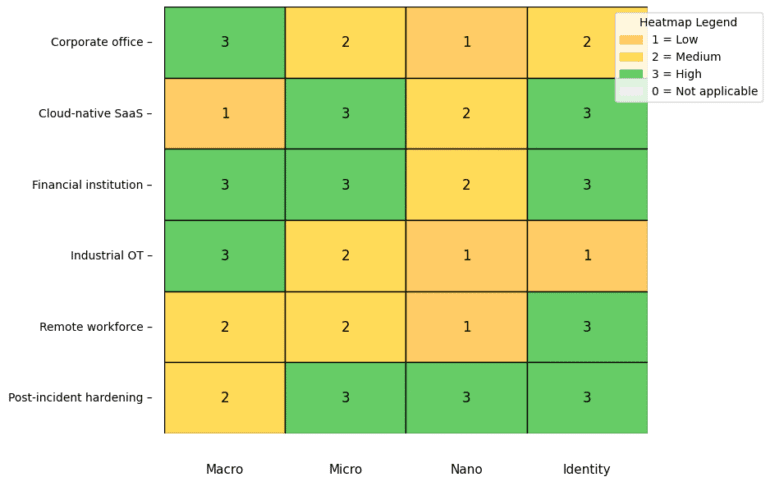
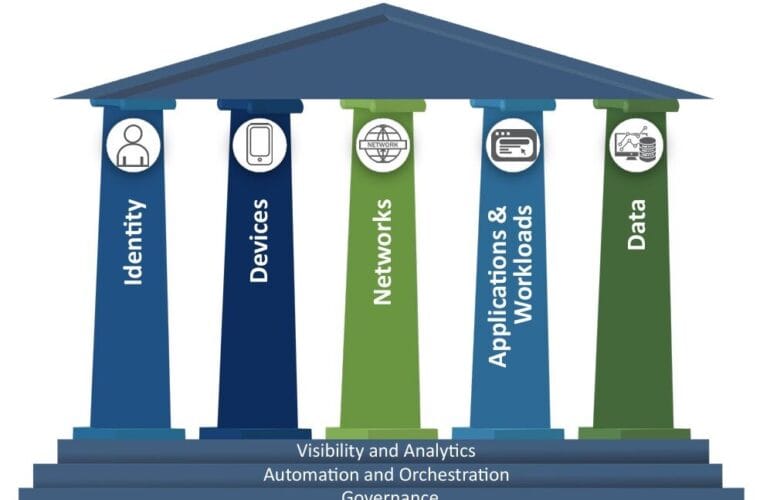
When you’re looking at integrating microsegmentation platforms into your existing security and network ecosystem, you’re aiming for more than just granular controls. You’re forging connections between policy, visibility, automation, and operations. A successful integration transforms siloed tools into a coordinated defense, reducing risk and boosting agility.
Integrating Microsegmentation – Architectural Alignment
Your first step is mapping the big picture. How does your microsegmentation solution fit within the broader network topology and security fabric?
- Network overlays and underlays
- Existing firewall and next-gen firewall deployments
- Virtualisation platforms and container orchestration
- Cloud vs. on-premises workloads
Each of these layers may use different tagging schemes, control planes, and enforcement points. Ensuring they speak the same language (VLAN IDs, VXLAN segments, security tags) is essential for policy consistency.
API and Protocol Compatibility
Integrations live and die by their APIs. Evaluate:
- RESTful or gRPC endpoints for policy creation and management
- Native connectors for SDN controllers (e.g., Cisco ACI, VMware NSX)
- Support for common automation tools (Ansible, Terraform)
- Rate limits, authentication mechanisms (OAuth2, certificates), and versioning
Plan for change: version upgrades can break connectors, so choose platforms with clear deprecation policies and robust SDKs.
Centralised Policy Orchestration
Microsegmentation shines when policies are managed centrally, not scattered across dozens of consoles.
- Integrate with your policy management hub (SIEM, SOAR, or CASB)
- Use a unified rule repository to avoid overlaps or conflicts
- Establish a source of truth for asset inventory and application flows
- Leverage tagging and dynamic groups for consistent policy application
This centralised approach reduces configuration drift and accelerates incident response.
Data and Telemetry Sharing
Visibility is the fuel that powers smart segmentation. Your microsegmentation platform must feed rich telemetry into:
- Security Information and Event Management (SIEM) systems
- Network performance monitoring tools
- Threat intelligence platforms
High-fidelity flow logs and process-level insights enable faster detection of lateral movement. Confirm that data formats (CEF, JSON, syslog) and transport mechanisms (TLS, Kafka) are aligned.
Identity and Endpoint Integration
Segmenting purely on IP and port doesn’t cut it in dynamic environments. Tie in identity and endpoint posture:
- Integrate with directory services (Active Directory, LDAP) for user and group context
- Leverage endpoint detection and response (EDR) tools to enforce posture-based micro perimeters
- Use identity-aware proxies or zero trust network access (ZTNA) solutions for workload and user authentication
This ensures policies adapt to who’s connecting, from which device, and under what security posture.
Automation and Orchestration
Manual policy updates are a recipe for errors. Embed your microsegmentation workflows into your automation pipelines:
- Build IaC modules for policy definitions
- Trigger policy deployments via CI/CD on application release
- Automate drift detection and remediation
- Use chat-ops or ticketing integrations to link approvals and audits
A closed feedback loop delivers faster, safer changes and reduces operational overhead.
Performance, Scalability, and Resilience
Microsegmentation can introduce latency or complexity if not designed for scale:
- Benchmark performance under normal and peak loads
- Confirm clustering, high-availability, and failover behaviors
- Plan for distributed enforcement across multiple data centers or clouds
- Monitor overhead on enforcement nodes and network paths
Scalability testing uncovers bottlenecks before production cuts over.
Compliance, Auditing, and Reporting
Your integration must support governance and audit requirements:
- Capture policy change histories and user approvals
- Generate compliance-ready reports for frameworks (PCI DSS, GDPR, ISO 27001)
- Ensure log retention policies align across platforms
- Embed identity and context in audit trails
Comprehensive reporting not only keeps auditors happy but also accelerates forensics.
Change Management and Training
A new segmentation layer changes how teams operate:
- Document end-to-end processes and tool interactions
- Provide role-based training for network, security, and DevOps teams
- Run workshops and tabletop exercises to simulate policy changes and incident response
- Establish a governance board to review integrations, policies, and exceptions
Well-prepared teams avoid configuration blind spots and miscommunications.
Ongoing Optimisation
Integration isn’t a one-and-done project. To maximise ROI:
- Continuously refine policies based on traffic analytics
- Expand integrations to new tools as your stack evolves
- Periodically reassess API compatibility and version upgrades
- Solicit feedback from incident responders and network operators
A living microsegmentation framework adapts to emerging threats and business needs.
Final Thoughts
Integrating microsegmentation goes beyond plugging in a new appliance or agent. It requires orchestrating policy, telemetry, identity, and automation across your security and network domains. By taking a holistic approach—aligning architectures, harmonising APIs, centralising policy, and prioritising performance—you’ll build a resilient, adaptable, and detectable perimeter around every workload.
Beyond these considerations, you might explore AI-driven policy recommendations, identity-centric zero trust frameworks, or advanced breach simulation tools. The future of segmentation is dynamic, contextual, and deeply integrated—make sure your architecture is ready to evolve.