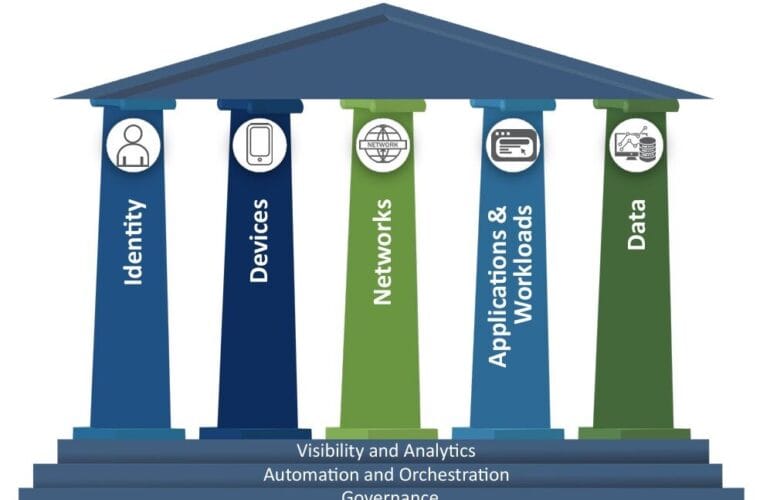
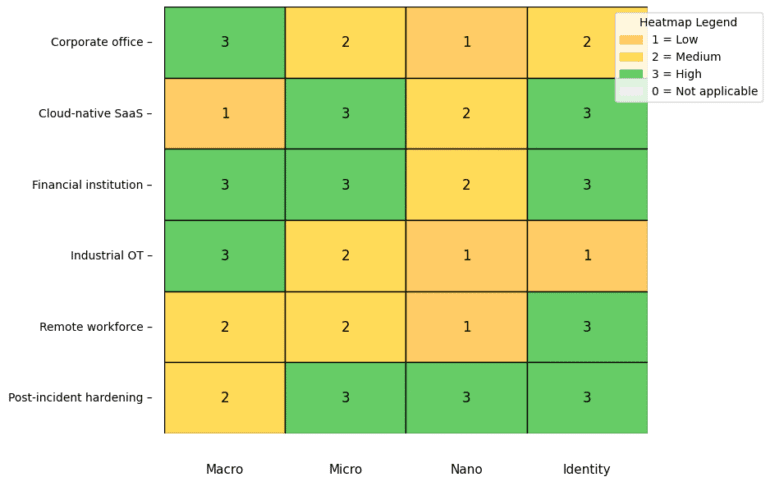
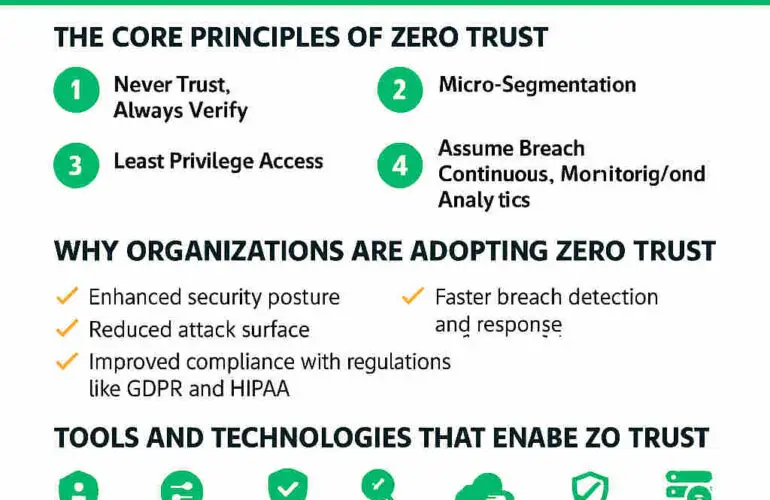
Deploying a microsegmentation platform and embedding it into your CI/CD workflow supercharges your security posture. You catch policy drift before code reaches production, automate guardrails, and turn segmentation into a living, versioned artifact.
Below, you’ll find the core considerations for architecting, coding, testing, and automating microsegmentation as part of a developer-first, shift-left strategy.
Define Your Security-as-Code Foundation
Every segment rule needs to live alongside application code, not in a separate console.
- Adopt a declarative policy language (YAML, JSON) that can be linted, reviewed, and versioned
- Store segmentation manifests in the same repo as your microservice definitions
- Enforce pull requests for policy changes with mandatory code reviews
Example YAML snippet for a pipeline stage:
stages:
- name: Build
- name: Security
- name: Deploy
jobs:
- stage: Security steps:
- script: |
policy-linter scan ./segmentation/policies
displayName: “Lint Micro-Segmentation Policies”
- script: |
Integrate Policy Validation into CI
Catching misconfigurations early saves weeks of firefighting later.
- Lint and syntax-check policies with a dedicated tool
- Run “dry-run” simulations against a staging environment
- Fail the build on high-severity violations (e.g., open east–west flows)
- Generate human-readable reports and post them to chat or ticketing systems
Automated gates ensure that no unreviewed rule ever moves forward.
Automate Testing of Microsegmentation Rules
Functional and vulnerability tests must encompass both code and network policy.
- Infrastructure-as-Code tests (e.g., Terraform plan) for policy changes
- Container-level connectivity checks (using tools like
netcator custom scripts) - Penetration-style tests in your ephemeral test clusters
- Chaos experiments to validate policy resilience under failure scenarios
This layered testing confirms that segmentation rules actually enforce the intended micro-perimeters.
Align with Application Topology and Dependencies
Your CI/CD integration should be topology-aware.
- Use service-mesh or orchestration metadata (labels, annotations) to auto-generate baseline policies
- Tag each workload with environment (dev, staging, prod) and tier (frontend, backend, database)
- Leverage dependency graphs to propose least-privilege rules during build time
Metadata-driven policy generation scales with your microservices fleet and reduces manual toil.
Enforce Runtime Telemetry and Feedback Loops
Shift-left isn’t a one-off milestone; it’s a cycle of continuous improvement.
- Instrument enforcement points to emit flow logs and policy violation events
- Ingest logs into your CI pipeline dashboards or observability tools
- Correlate runtime anomalies back to policy definitions in Git commits
- Trigger automated rollback or patch releases when unauthorised lateral traffic is detected
Real-time feedback keeps segmentation aligned with evolving application behavior.
Embed Authorisation and Identity Context
Microsegmentation only reaches its full potential when it’s identity-aware.
Identity integration ensures policies adapt to who or what is connecting, not just IPs.
Manage Secrets and Certificates Securely
Your segmentation agents and orchestrators need credentials to talk to APIs.
- Store certificates and API tokens in a secrets manager (Vault, AWS Secrets Manager)
- Inject secrets into CI jobs via ephemeral, scoped credentials
- Rotate keys automatically as part of your pipeline’s release process
This tight control prevents credentials from becoming network policy blind spots.
Implement Change Management and Audit Trails
CI-driven changes must remain transparent and traceable.
- Tag every deployment with pipeline run IDs and Git commit hashes
- Push audit logs to centralised SIEM systems for compliance reporting
- Generate “who-did-what-when” drilldowns that link code changes to policy updates
Robust audits mean you can prove governance without manual log digging.
Train Teams and Foster a Security-First Culture
Shifting left is as much about mindset as it is about tooling.
- Host workshops on writing policy-as-code and local testing
- Appoint security champions in each development squad
- Run regular “policy dojo” sessions where teams practice breaking and fixing segmentation
Investment in developer skills makes guardrails feel like enablers, not roadblocks.
Plan for Scalability and Evolution
Your CI/CD pipeline will grow. Make sure your microsegmentation integration can, too.
- Modularise pipeline steps into reusable templates or shared libraries
- Monitor pipeline performance and parallelise heavy security checks
- Version your policy-as-code modules and maintain backward-compatibility
Evolving your pipeline ensures security scales with the pace of innovation.
Wrapping Up
By baking micro segmentation into your CI/CD processes, you transform policies from afterthoughts into first-class artifacts. You catch drift before deployment, automate compliance, and give developers the tools to own security.
To go further, consider:
- AI-powered policy suggestion engines that learn from your traffic patterns
- Continuous breach-and-attack simulation integrated into your pipeline
- Expanding shift-left to cover secrets scanning, container CVE checks, and infrastructure drift detection
- Building a community of practice to share patterns and policy templates across teams
Shifting security left isn’t just a technical journey—it’s a cultural revolution. Start small, iterate quickly, and watch your micro-segmentation practices mature alongside your products.