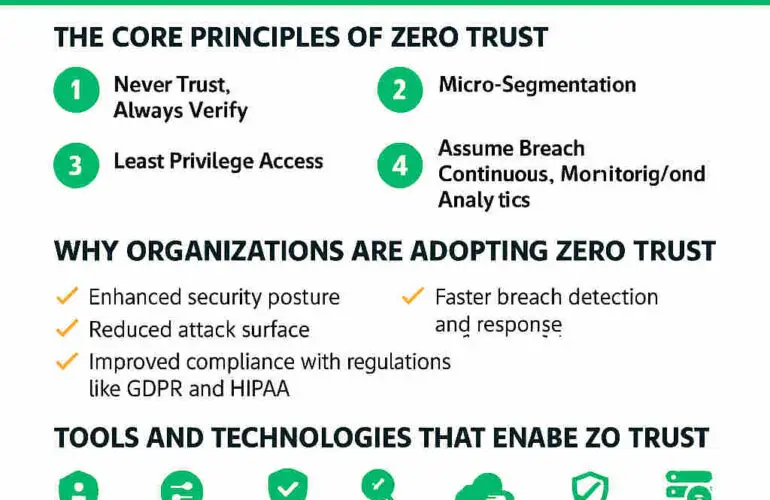
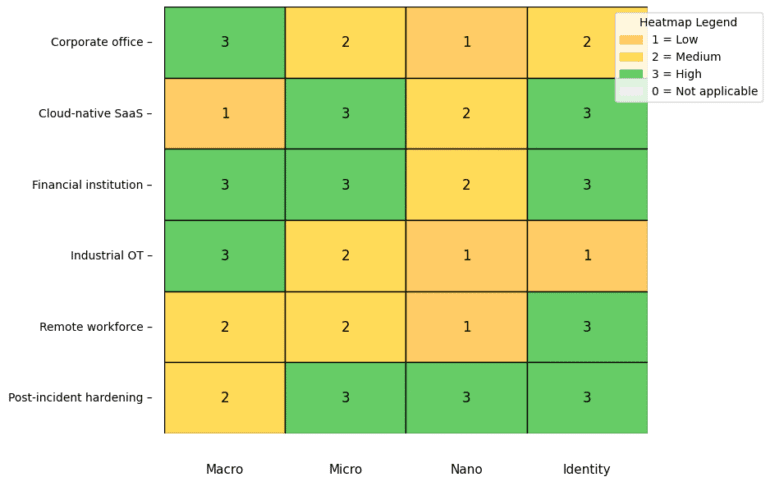
🔑 Step 1: Define Your Zero Trust Vision and Objectives
• Firstly clarify business drivers: Are you aiming to protect sensitive data, meet compliance requirements, or reduce insider threats?
🗺 Step 2: Assess Your Current Security Posture
You can’t build a roadmap without knowing where you stand.
• Inventory assets: Catalog users, devices, applications, and data flows
• Evaluate existing controls: Identify gaps in identity management, endpoint protection, and network segmentation
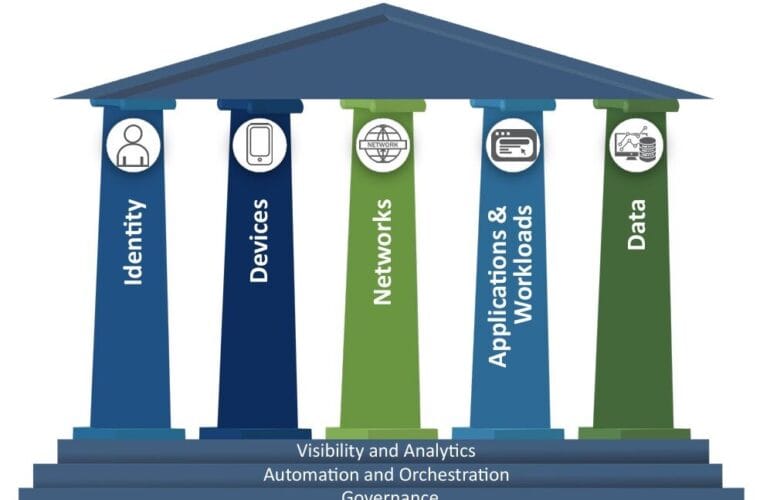
🧩 Step 3: Establish Core Zero Trust Pillars
🛠 Step 4: Prioritise Quick Wins and Long-Term Goals
A Zero Trust journey can feel overwhelming, so break it down:
compliance
• Medium-term goals: Implement microsegmentation, adopt cloud-native security tools, and enhance monitoring
🤝 Step 5: Build a Cross-Functional Team
• IT & Security teams: Lead technical implementation
• Compliance & Legal: Ensure regulatory alignment
• Business units: Provide input on workflows and user experience
• Executive leadership: Drive cultural adoption and funding
📊 Step 6: Develop a Phased Roadmap
• Phase 1: Foundation – Identity, MFA, device compliance
• Phase 2: Expansion – Network segmentation, workload protection
• Phase 3: Optimisation – Automation, AI-driven analytics, continuous improvement
🔄 Step 7: Continuously Monitor and Adapt
• Regular audits: Validate controls and policies
• Threat intelligence: Stay ahead of emerging risks
• Feedback loops: Adjust policies based on user experience and business needs