Cyber Security in an Acquisition: 7 Costly M&A Mistakes to Avoid
When two companies merge, the spotlight often falls on market expansion, revenue synergy, or cost reduction. However, cyber security is a critical factor that can determine the success or failure of mergers and acquisitions (M&A). Effective strategies are essential for managing cyber risk and ensuring a smooth transition. In today’s digital landscape, the consequences of neglecting cyber security during an acquisition can be severe, ranging from regulatory fines to reputational damage and operational disruption.
Without robust due diligence, a promising deal can quickly devolve into a costly clean-up operation. M&A events are prime targets for cyberattacks and insider threats due to increased data flow and organisational uncertainty. Recent industry reports show that nearly 40% of M&A deals experience a cyber incident during the transaction process, highlighting the urgent need for comprehensive security planning. For more research and trends, see our cyber security insights.
Cyber Security in an Acquisition: Due Diligence Essentials
Security due diligence should begin before legal and financial negotiations conclude. Buyers must assess the risks they’re inheriting. Key steps for posture management include:
- Infrastructure Mapping: Identify servers, endpoints, SaaS tools, cloud environments, and legacy systems. This provides a clear view of the digital assets at stake and helps prioritise integration efforts.
- Data Landscape: Understand the types, locations, and protections of personal, financial, and proprietary data. Data discovery tools can automate this process, ensuring no critical information is overlooked.
- Third‑Party Dependencies: Review vendor relationships and third‑party security assessments to manage external risks. Supply chain vulnerabilities are a common entry point for attackers.
- Incident History: Request records of past breaches or data leaks. Analysing previous incidents can reveal recurring weaknesses and inform remediation plans.
Approach this phase like a red‑team assessment—comprehensive and adversarial in mindset. Best practices involve thorough checks and proactive risk identification.
Additionally, consider performing penetration testing and vulnerability assessments where permitted. These technical evaluations provide a realistic picture of the target company’s security posture and help prioritise remediation efforts.
For a comprehensive overview of legal frameworks and compliance in M&A, read the ICLG’s M&A laws and regulations report.
Legal Boundaries Around Information Gathering
Legal constraints can complicate security assessments. Non‑disclosure agreements and regulatory obligations may limit access to sensitive data. Unauthorised penetration testing is strictly prohibited. It’s essential to work closely with legal counsel to ensure all activities comply with relevant laws and regulations.
Use controlled data rooms and document exchanges with explicit consent for deeper assessments. Under GDPR, personal data must be anonymised or aggregated unless a lawful basis exists. Legal compliance is essential to avoid penalties and ensure smooth post-acquisition data protection. In cross-border deals, be mindful of differing privacy laws and data residency requirements, which may impact how information is shared and stored.
Case studies have shown that failure to comply with data protection regulations can result in multi-million-pound fines and protracted legal disputes. Establishing clear protocols for data access and transfer is a vital part of the due diligence process. For official guidance, see the ICO’s guidance on due diligence and data sharing in mergers and acquisitions.
Post-Acquisition Protection Strategies
After the deal closes, the buyer must extend their security posture to the acquired entity. Legacy systems and inconsistent controls are common challenges. A structured integration roadmap includes:
- Assessment Phase: Review asset inventory, vulnerabilities, IAM, tech stack, and monitoring. This helps identify gaps and prioritise remediation.
- Prioritisation: Address critical gaps first, focusing on high-risk assets and processes.
- Policy Alignment: Harmonise with frameworks like ISO 27001 or NIST to ensure consistent standards across the organisation.
- Tooling and Controls: Decide between extending or consolidating security tools for stack alignment. This can reduce complexity and improve visibility.
- Continuous Monitoring: Track improvements using posture management tools and regular audits.
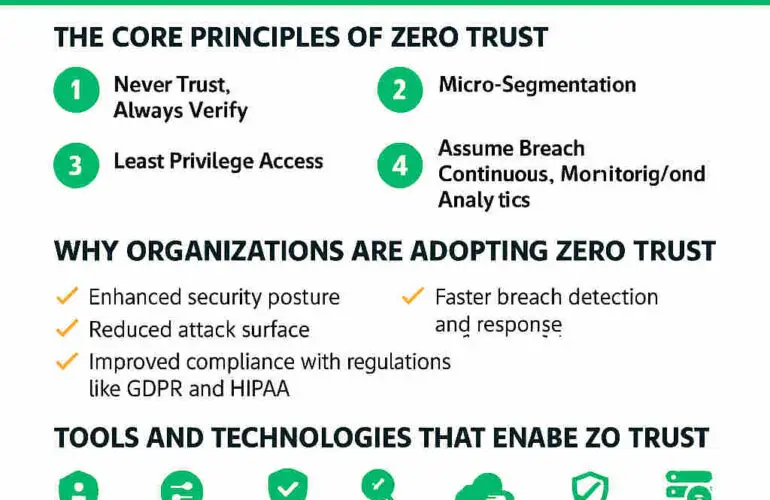
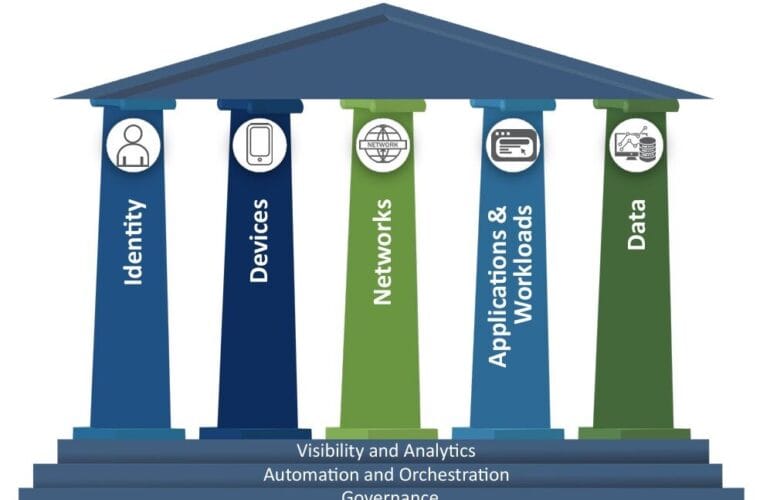
Challenges of legacy systems in acquired companies can be mitigated with a clear roadmap and ongoing monitoring. It’s also important to provide training and awareness programmes for staff, as human error remains a leading cause of security incidents. For more, see our article on preparing a zero trust roadmap and how best to approach a zero trust implementation.
Consider establishing a joint incident response team to handle any breaches or suspicious activity during the integration phase. This ensures rapid detection and containment, minimising potential damage.
For ongoing monitoring and improvement, see our guide to continuous threat exposure management. For practical advice on integrating and closing data protection gaps after an acquisition, explore Bird & Bird’s post-acquisition data protection integration guide.
Managing Insider Threats During M&A
Acquisitions create uncertainty, increasing insider risk. Mitigating these threats requires a combination of technology and culture. Strategies include:
- Access review: Audit and disable dormant privileged accounts to prevent unauthorised access.
- Monitoring: Enhance logging on critical systems to detect suspicious behaviour.
- Separation of duties: Prevent unilateral system changes by enforcing role-based access controls.
- Communication: Transparent messaging reduces anxiety and discourages malicious actions.
- Offboarding protocols: Reaffirm NDAs and disable accounts promptly when employees leave.
Culture plays a vital role in insider risk management—technology alone isn’t enough. Encourage open dialogue and provide support for employees during the transition to reduce the likelihood of disgruntled insiders.
Recent examples show that companies with strong insider threat programmes experience fewer incidents and recover more quickly from breaches. Investing in employee engagement and training pays dividends in overall security. For best practices, see INSA’s executive summary on managing insider risk during M&A.
Tooling Alignment – One Stack or Two?
Security stack alignment is essential but delicate. A phased approach works best:
- Bridge: Integrate both toolsets into a unified reporting layer to maintain visibility during the transition.
- Consolidate: Choose the dominant stack based on scalability and familiarity, reducing operational overhead.
- Optimise: Re‑baseline detections and alerts post‑integration to ensure accurate monitoring.
Aligning security tools after an acquisition ensures efficiency and fosters cultural alignment and adoption. Involve representatives from both organisations in decision-making to build consensus and encourage buy-in.
Regularly review and update your security architecture to adapt to evolving threats and business needs. Automation and orchestration tools can help streamline processes and improve response times. For strategic planning, see prepare a zero trust roadmap and approach to implementing zero trust.
For a foundational overview, read what is zero trust and redefining the network security perimeter in a zero trust world. For identity security and stack alignment during M&A integration, read Delinea’s identity security guide. For mapping your stack to a security framework, see Blackpoint’s article.
Final Thoughts – Cyber Risk Is Deal Risk
Security due diligence is as critical as financial audits. Engage CISO‑level experts early, plan data sharing lawfully, manage insider threats proactively, and align tooling with strategic intent. Managing cyber security during mergers and acquisitions is a question every business leader should ask before, during, and after the deal.
Steps for cyber security assessment in M&A deals and continuous monitoring of security posture after acquisition are essential for long-term success. By prioritising cyber security at every stage of the transaction, organisations can protect their investments, maintain stakeholder trust, and achieve their strategic objectives.
In summary, the most successful M&A deals are those where cyber security is treated as a core business priority, not an afterthought. With the right approach, you can avoid costly mistakes and set the stage for sustainable growth. For further reading on data protection integration, see Bird & Bird’s guide.