How to Measure Zero Trust Maturity: A Practical Guide for Organisations
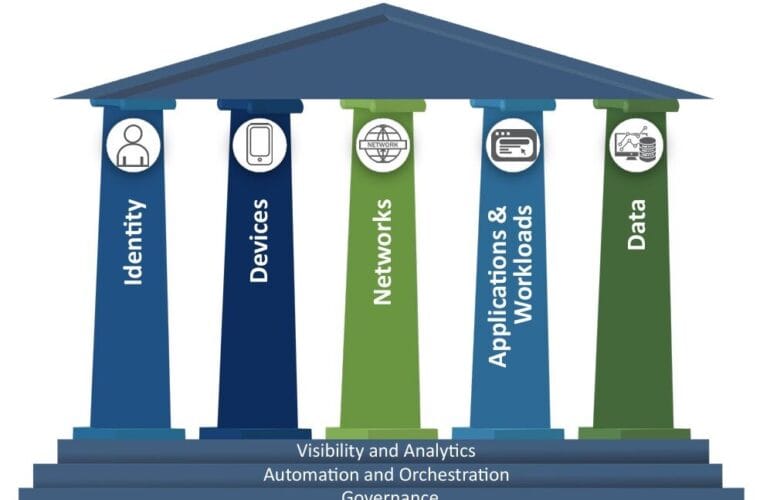
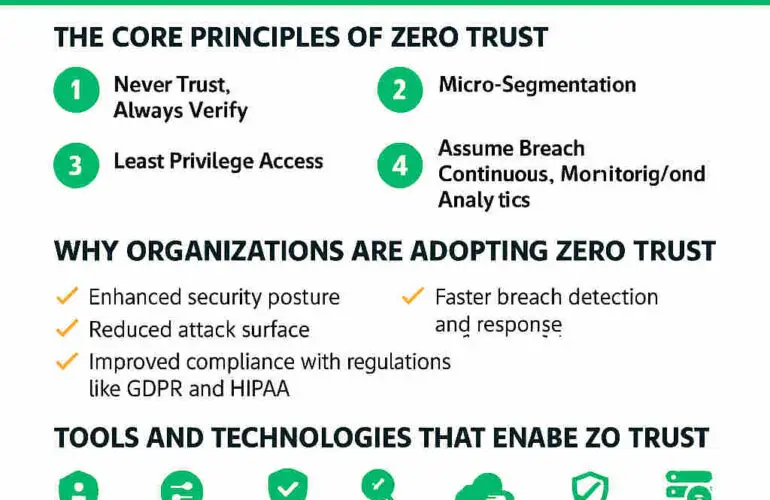
Many organisations are seeking the best way to measure Zero Trust maturity and assess their readiness for adopting Zero Trust principles. Zero Trust maturity is a journey—a security roadmap focused on measurable improvements in security posture. The core tenets include: never trust, always verify; least privilege; assume breach; micro-segmentation; identity-driven access; continuous monitoring and analytics; and data protection through classification, encryption, and rights management.
Current Industry Position in the UK and Internationally
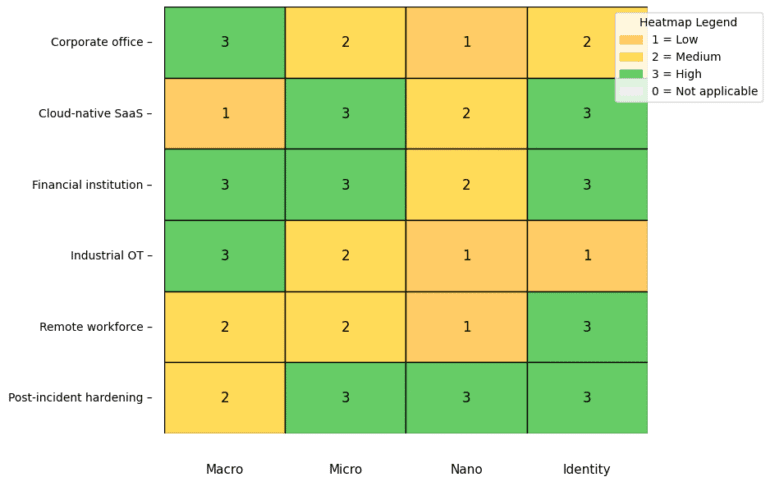
Across sectors, Zero Trust maturity varies. Many organisations have adopted elements such as strong identity and access management (IAM), multi-factor authentication (MFA), endpoint detection, and cloud controls. However, enterprise-wide Zero Trust is still uncommon. Strengths include widespread MFA, cloud-native identity and policy controls, and modern endpoint detection and response (EDR/XDR). Weaknesses persist in legacy systems, flat network architectures, incomplete visibility, and fragmented toolsets. Cultural and governance barriers are as significant as technical limitations.
Larger enterprises with cloud-first programmes and dedicated security budgets are better placed to transform. Small and medium-sized organisations can reduce risk by focusing on identity, critical data protection, and high-risk services.
Measuring Zero Trust Maturity
Maturity should be assessed across technical and organisational domains. A practical framework covers five areas:
-
Identity and Access Management
- Basic: password-based access, sporadic MFA
- Intermediate: single sign-on, role-based access control, adaptive MFA
- Advanced: continuous risk-based authentication, contextual policies, delegated administration
-
Device and Endpoint Security
- Basic: anti-malware, routine patching
- Intermediate: EDR with automated containment, device posture checks
- Advanced: device attestation, managed certificates, policy enforcement tied to device health
-
Network and Application Controls
- Basic: perimeter firewalls, VPNs
- Intermediate: micro-segmentation for critical apps, software-defined perimeters
- Advanced: service mesh, application-level access control, granular east-west encryption, policy enforcement
-
Data Protection
- Basic: encryption at rest, ad hoc access reviews
- Intermediate: systematic data classification, DLP, rights management
- Advanced: persistent data-centric protections, attribute-based access controls, lifecycle controls
-
Visibility, Analytics and Automation
- Basic: centralised logging, manual review
- Intermediate: SIEM with correlation, threat hunting, standardised incident workflows
- Advanced: UEBA, SOAR-driven playbooks, automated policy adjustments
Organisations ready to execute a Zero Trust programme are typically at least intermediate across these domains and have a clear roadmap to address remaining gaps.
Common Gaps in Zero Trust Readiness
- Incomplete identity coverage (legacy accounts, unmanaged credentials, privileged accounts)
- Deficient asset and data inventory
- Policy sprawl and interoperability issues
- Over-reliance on network location and VPNs
- Third-party and supply chain exposure
- Limited telemetry and analytics maturity
These gaps are rarely about missing technology—they’re about incomplete execution, lack of integration, weak governance, and insufficient prioritisation.
Practical Steps to Increase Zero Trust Maturity
- Start with identity as the control plane: consolidate providers, implement adaptive MFA, automate credential management
- Move service accounts and secrets into managed stores, automate rotation and approvals
- Build reliable asset and data inventories with automated discovery
- Classify data by sensitivity, map data flows
- Adopt least privilege incrementally, apply role- and attribute-based access controls for high-value resources
- Implement just-in-time privilege for administrators, monitor privileged sessions
- Segment networks and applications pragmatically, begin with crown-jewel assets
- Use service mesh, application gateways, or software-defined perimeters for cloud-native workloads
- Centralise logs, enrich events with context, deploy UEBA for anomaly detection
- Build SOAR playbooks for automated incident response
- Align governance, policy, and risk appetite; establish cross-functional governance
- Pilot, measure, and iterate; track metrics like time-to-detect, time-to-contain, reduction in privileged access, coverage of critical assets
- Manage third-party risk actively, require vendor integration with identity controls, monitor vendor activity
Summary & Recommended Next Steps
Zero Trust is both a technical architecture and an organisational transformation. Most organisations have foundational elements for a pragmatic Zero Trust programme, especially in identity and cloud controls. Full enterprise-wide Zero Trust remains aspirational due to legacy estates, visibility gaps, and governance challenges. The sensible approach is incremental: treat identity and data as primary levers, automate discovery and classification, prioritise least privilege for high-value resources, and use pilots to prove value while aligning stakeholders.
For UK organisations, early focus on vendor constraints, data classification, and auditability will accelerate compliance and security benefits. A multi-year investment in integration, telemetry, and automation will improve resilience and threat response.
Frequently Asked Questions
- What is Zero Trust maturity?
- It’s a measure of how comprehensively an organisation has adopted Zero Trust principles across identity, devices, networks, applications, and data.
- How do I start measuring Zero Trust maturity?
- Assess your organisation across the five key domains: identity, endpoints, network, data, and analytics. Use a framework to rate your current state and identify gaps.
- What are the most common gaps?
- Legacy accounts, incomplete inventories, policy sprawl, over-reliance on network location, third-party risk, and limited analytics.
- How can small organisations improve Zero Trust maturity?
- Focus on identity controls, critical data protection, and phased adoption of Zero Trust practices.