Need help understanding Zero Trust Maturity Models?
In today’s rapidly evolving cyber threat landscape, organisations can no longer rely on traditional perimeter-based defences. The concept of Zero Trust—“never trust, always verify”—has become the cornerstone of modern cybersecurity strategies. To help organisations adopt and measure progress in Zero Trust, several UK and US government agencies have developed Zero Trust maturity models, each offering unique perspectives and frameworks. The three most influential are from the Department of Defense (DoD), the Cybersecurity and Infrastructure Security Agency (CISA), and the National Security Agency (NSA).
This article explores these models in depth, highlighting their pillars, maturity stages, and practical implications for organisations seeking to strengthen their cybersecurity posture.
What is Zero Trust?
Zero Trust is a security model that assumes threats can originate both inside and outside the network. Instead of granting implicit trust based on location or credentials, Zero Trust requires continuous verification, least-privilege access, and granular enforcement of security policies. The goal is to minimise the attack surface, prevent lateral movement, and ensure that only authorised users and devices can access sensitive resources.
Department of Defense (DoD) Zero Trust Maturity Model
The DoD Zero Trust Strategy and Reference Architecture provides a comprehensive roadmap for implementing Zero Trust across the defence enterprise. Released in 2022 and updated through subsequent directives, the DoD model emphasises cultural adoption, technical acceleration, and enterprise-wide enablement.
Key Pillars
The DoD identifies seven pillars of Zero Trust:
- User – Continuous authentication and conditional access.
- Device – Uniform device hygiene and compliance.
- Application & Workload – Segmentation and secure application deployment.
- Data – Encryption, tagging, and data-centric protections.
- Network & Environment – East-west segmentation, VPN-less access.
- Visibility & Analytics – AI-driven monitoring and anomaly detection.
- Automation & Orchestration – Dynamic policy enforcement and centralised orchestration.
Maturity Approach
The DoD maturity model is less about rigid stages and more about capability adoption across pillars. Each pillar has defined capabilities, ranging from basic controls (like multi-factor authentication) to advanced measures (like dynamic, continuous authorisation). The DoD roadmap sets a target of full Zero Trust implementation by 2027, with milestones for cultural adoption, technology deployment, and synchronisation across components. A detailed overview of the DOD's Zero Trust Execution Roadmap can be found here.
Strategic Goals
- Cultural Adoption – Training personnel to embrace Zero Trust principles.
- Secured Systems – Integrating Zero Trust into both legacy and new systems.
- Technology Acceleration – Deploying cutting-edge tools at pace with industry.
- Enablement – Aligning funding, policies, and processes with Zero Trust.
CISA Zero Trust Maturity Model
The CISA Zero Trust Maturity Model (ZTMM), first released in 2021 and updated to Version 2.0 in 2022, provides a structured roadmap for federal civilian agencies but is widely adopted across industries.
Five Pillars
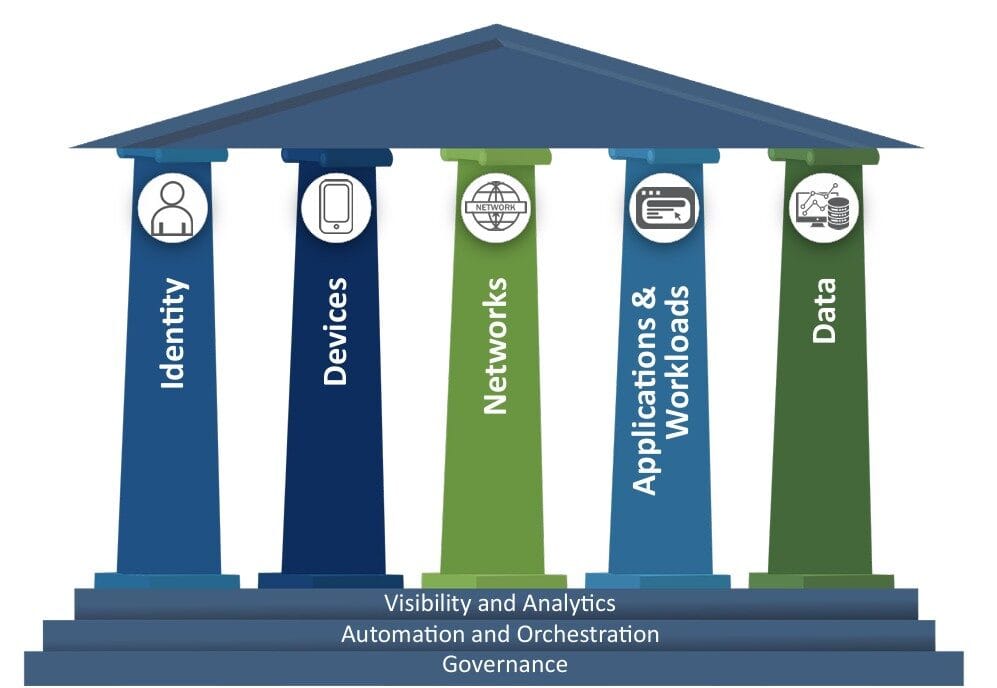
CISA organises Zero Trust into five protection areas:
- Identity – Strong authentication and lifecycle management.
- Devices – Secure, compliant devices across the enterprise.
- Networks – Segmentation, monitoring, and secure communications.
- Applications & Workloads – Secure development and workload isolation.
- Data – Encryption, tagging, and access control.
To illustrate its Zero Trust Maturity Model Pillars CISA provides the following image:
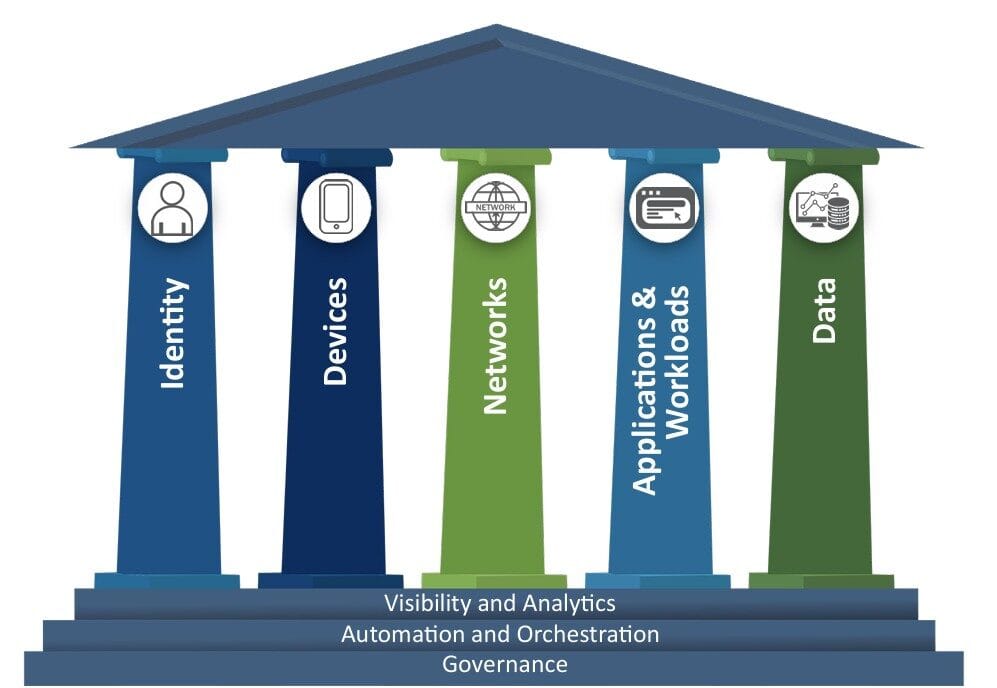
Cross-Cutting Capabilities
- Visibility & Analytics
- Automation & Orchestration
- Governance
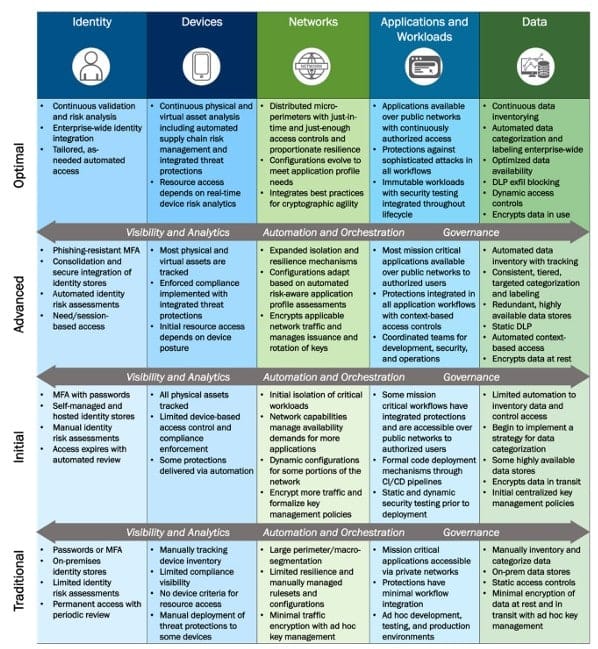
Four Maturity Stages
CISA defines four stages of maturity:
- Traditional – Perimeter-based, siloed security.
- Initial – Early automation, least-privilege strategies, and visibility.
- Advanced – Centralised identity, integrated policy enforcement, near real-time risk assessments.
- Optimal – Fully automated lifecycle management, dynamic just-in-time (JIT) and just-enough-access (JEA), continuous monitoring.
Practical Use
CISA’s model is highly prescriptive, offering agencies a way to assess current posture, identify gaps, and plan incremental improvements. It aligns with federal mandates like OMB M-22-09, making it a benchmark for compliance and modernisation.
NSA Zero Trust Maturity Guidance
The NSA Zero Trust maturity guidance takes a more technical, pillar-specific approach. Rather than a single overarching model, the NSA publishes Cybersecurity Information Sheets (CSIs) that provide detailed recommendations for maturing specific pillars.
Pillar-Specific Guidance
NSA focuses on advancing maturity across seven pillars, similar to DoD:
- User Pillar – Continuous identity verification.
- Device Pillar – Secure device management.
- Network & Environment Pillar – Segmentation, data flow mapping, software-defined networking.
- Data Pillar – Catalogue, encryption, granular access control, monitoring.
- Application & Workload Pillar – Secure coding and workload isolation.
- Visibility & Analytics Pillar – Real-time anomaly detection.
- Automation & Orchestration Pillar – Integrated, automated policy enforcement.
Maturity Recommendations
NSA guidance emphasises:
- Micro-segmentation to contain adversarial lateral movement.
- Granular data attributes for access control.
- Continuous monitoring to detect anomalous activity.
- Interoperability to ensure secure data sharing across organisations.
Unlike CISA’s staged model, NSA’s approach is modular and technical, offering actionable steps for organisations to mature specific capabilities depending on their risk profile.
Comparing the Models
| Agency | Focus | Structure | Maturity Stages | Unique Features |
|---|---|---|---|---|
| DoD | Enterprise-wide defence adoption | 7 pillars | Capability-driven, FY2027 roadmap | Cultural adoption, military-grade use cases |
| CISA | Federal civilian agencies, industry | 5 pillars + 3 cross-cutting | Traditional → Optimal (4 stages) | Prescriptive, compliance-aligned |
| NSA | Technical, pillar-specific | 7 pillars | Modular guidance | Deep technical recommendations, CSIs |
Conclusion
Zero Trust is no longer optional—it is the foundation of modern cybersecurity. The DoD, CISA, and NSA maturity models each provide valuable frameworks:
- DoD emphasises cultural adoption and enterprise-wide enablement.
- CISA offers a staged roadmap for agencies to measure progress.
- NSA delivers technical, pillar-specific guidance to counter advanced threats.
Organisations should not view these models as competing but rather as complementary. Together, they provide a holistic blueprint for achieving Zero Trust maturity—balancing strategy, compliance, and technical depth.
By leveraging these models, enterprises can build resilient architectures that withstand evolving adversary tactics, protect sensitive data, and enable secure collaboration in an increasingly interconnected world.