
Insourcing vs Outsourcing IT Security Services in a Corporate Environment
Insourcing vs Outsourcing IT Security Services in a Corporate Environment:…
Accomplished cyber security consultancy with over 25 years of experience of progressive leadership driving strategic cyber and security transformation across global organisations.
Whether its reviewing, designing or executing cyber strategies & roadmap we will be able to guide your business safely throughout.


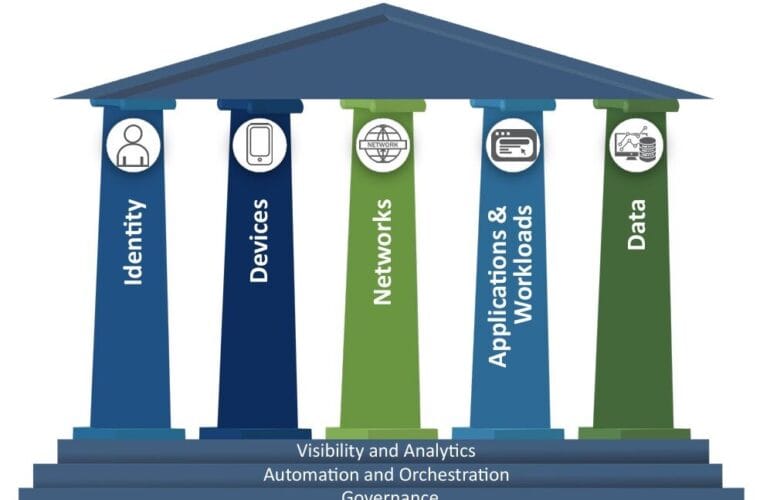
Need help understanding Zero Trust maturity models? The three most influential are from the Department of Defense (DoD), CISA, and the NSA.
