Insourcing vs Outsourcing IT Security Services in a Corporate Environment: Choosing the Right Cybersecurity Strategy Cybersecurity has...
What is Continuous Threat Exposure Management? Continuous Threat Exposure Management (CTEM) is a modern cybersecurity framework that...
5 Key Strategies for Lateral Movement Defence in Network Security When cybercriminals gain access to an organisation’s...
Introducing Identity and Access Management (IAM) What is IAM? – Identity and Access Management (IAM) is a...
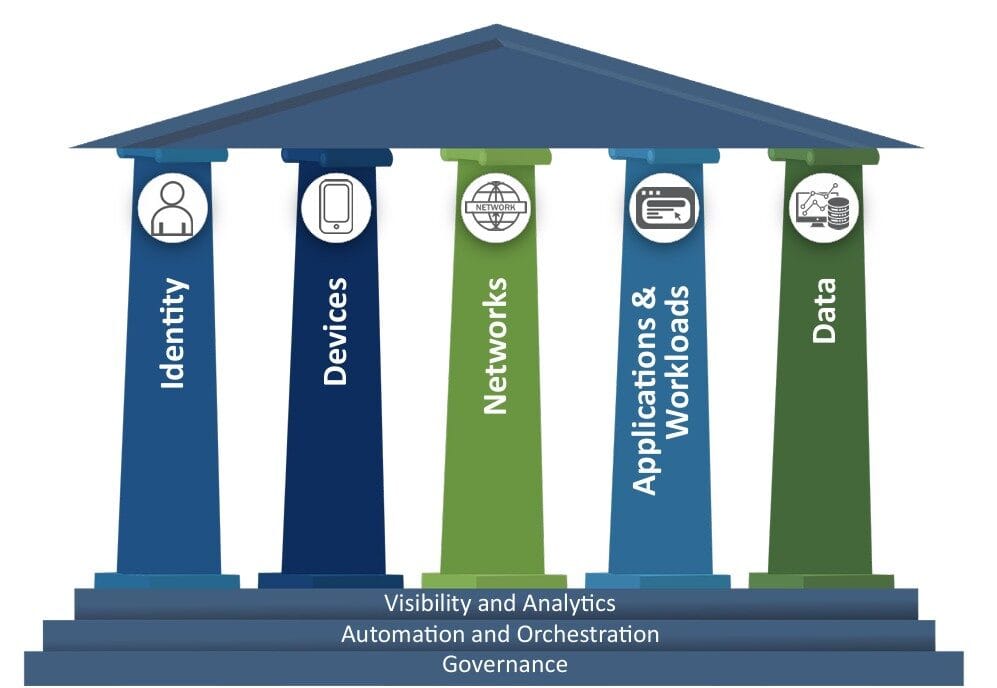
Understanding NIST’s Zero Trust Architecture and Its Key Elements What is NIST? NIST’s Special Publication 800-207 defines...
Zero Trust Security: Principles, Technologies & Implementation Guide What Is Zero Trust Security? This modern cybersecurity framework...