Cyber Security in an Acquisition: 7 Costly M&A Mistakes to Avoid When two companies merge, the spotlight...
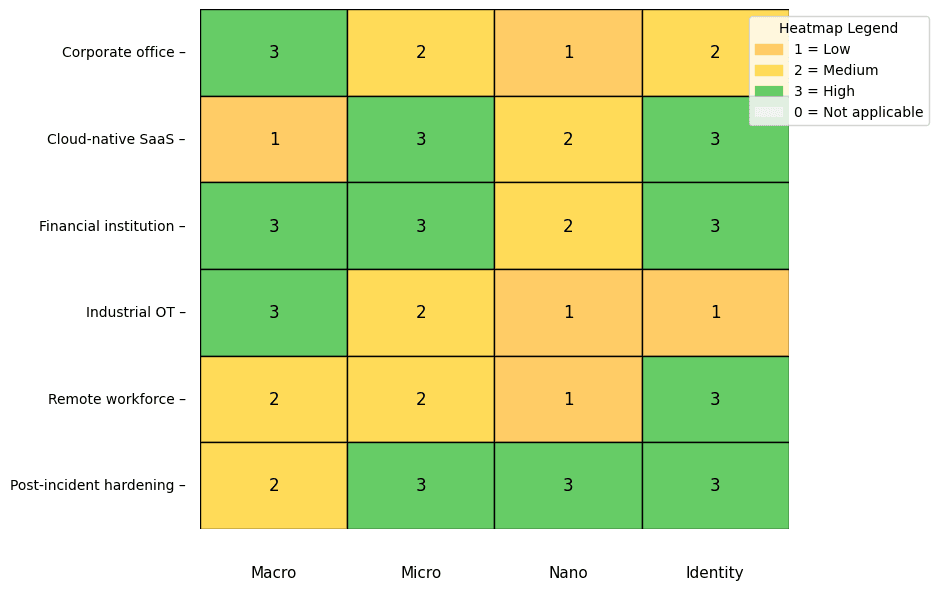
An in-depth guide to effective network segmentation strategies for corporate networks and when to use macro, micro,...
5 Key Strategies for Lateral Movement Defence in Network Security When cybercriminals gain access to an organisation’s...
New technology concepts and working practices are redefining the network security perimeter in a zero trust world....
Selecting the right microsegmentation solution can be tricky, we take a look at the top microsegmentation vendors...
Category
>>
Date Posted