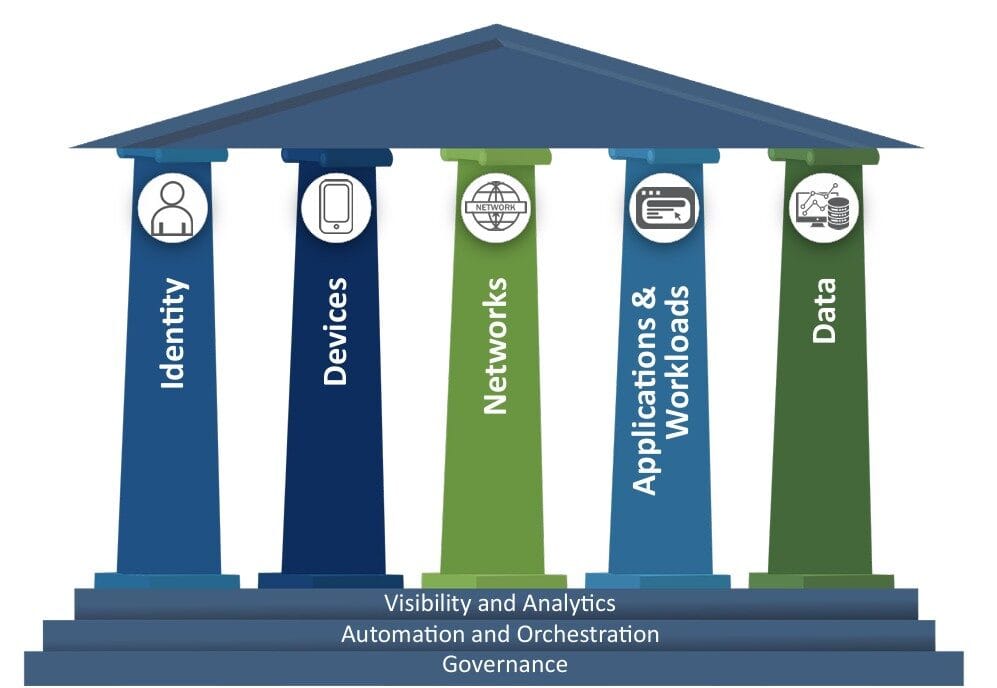
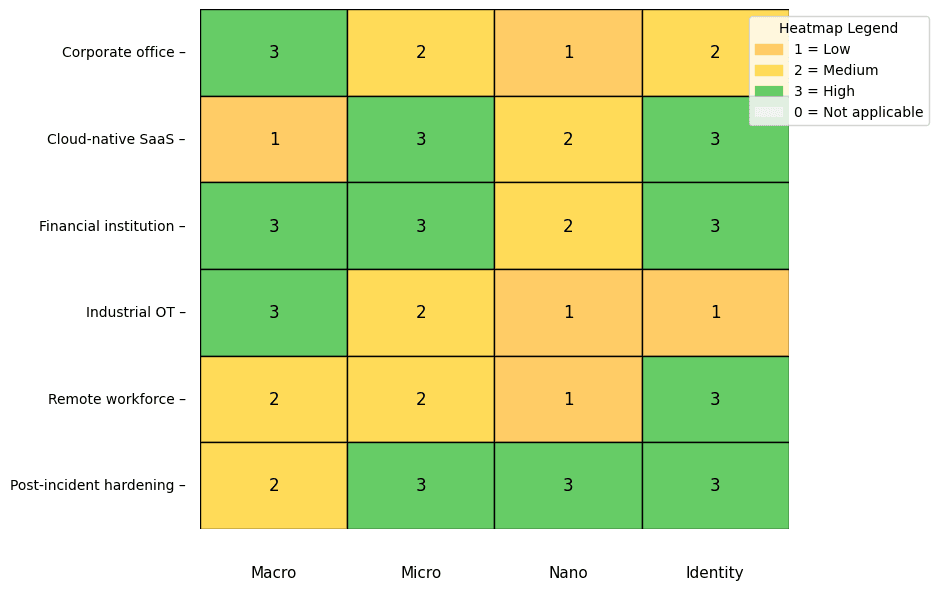
How to Measure Zero Trust Maturity: A Practical Guide for Organisations Many organisations are seeking the best...
9 Best Practices for Identity Data Quality in IAM and IGA Identity Data Quality in IAM and...
5 Key Strategies for Lateral Movement Defence in Network Security When cybercriminals gain access to an organisation’s...
Selecting the right microsegmentation solution can be tricky, we take a look at the top microsegmentation vendors...
Don’t know where to start when it comes to preparing your Zero Trust Roadmap? This guide walks...
Deploying a microsegmentation platform and embedding it into your CI/CD workflow supercharges your security posture. You catch...
When you’re looking at integrating microsegmentation platforms into your existing security and network ecosystem, you’re aiming for...
Zero Trust Security: Principles, Technologies & Implementation Guide What Is Zero Trust Security? This modern cybersecurity framework...